-
Asset Categorization and CMMC

Many Certified CMMC Professional (CCP)will find the Configuration Management domain one of the trickiest for organization seeking certification to implement. Yet you have to ensure all employess have secure equipment from the starting line. By spelling out clear rules of the road through policieis and procedures you can ensure all clients
The 11 practices, six from level 2, three from level 3 and one level five requirement focus on how an organization deploys, sets up and manages systems, devices, software, networks and hardware. Specifically on an organizations ability have a configuration baseline and practices to audit this configuration and introduce changes.
Why Configuration Management
A CCP will want to work with clients to develop configuration management policies and procedures to mitigate security risks. You cannot eliminate vulnerabilities and reduce the costs of systems maintenance without a good configuration management. Every device you give an employee, every network router, and every switch needs to follow specific set up in a consistent manner. A Certified CMMC Professional will needs to work with a client to manage all changes. This will require organizations seeking certification to develop defined change control process.
Imagine if you allowed employees to simply go online and order a laptop. How would you know what Operating Systems get used? Will you know if they update the computer? Which anti-virus software comes installed?
Configuration management limits these issues. A company must have standard baseline image, not just for devices but for all the endpoints. Your configuration management and change logs need to track the software version, any hardware or software installed, ports that get open or blocked, and protocols for vulnerability scanner that the user does not control.
Configuration Management takes deep technical knowledge. A CCP will need to work with software documentation, vulnerability scanning software, STIGS, Reference architecture from an external service provider, or often a checklists of steps to follow
In fact, talented CCPs will see configuration more as a life cycle approach rather than a simple security management checklists. This lifecycle moves a system from the concept of operations through the vulnerability scanning, change management, operations, and decommissioning. As a system matures the people in a company will come and go. New technologies will emerge. A CCP can help clients address these programs by ensuring they have a consistent change management policy through the lifecycle of the system that boils down to system hardening, change management, and change management processes.
You cannot accept the defaults. Rarely will products come out of the box with secured to a a NIST-SP-800-171 baseline. A CCP will work with clients to ensure service packs get updated, unnecessary features get deactivated, account provisioning stays in compliance, and all firewalls and automatic updates get set up. If an organization seeking certification inherits many of these practices from an external service provider such as an MSP or IT form the CCP will need to review the shared responsibility matrix.
The configuration management lifecycle requires a focus on change management. You must ensure systems remain stable and employees cannot make changes without privileged access. As a CCP make sure clients include change management in their configuration policies. An Organization Seeking Certification must have a formal review proposed for all changes. This should include regularly scheduled reviews and an emergency process for installing critical patches. Only these proposed changed should get made. Finally, a CCO should ensure a client as procedures in place to re-assess their baseline setting and ti evaluate if it should change.
In order for these first two elements of configuration management lifecycle to occur a CCP will need to assist companies in tracking the process through change logs. This includes having a change request process, evaluating the risk of change, an approval process, testing the change, evaluating if employees need new training, implementing a baseline, validating the baseline, and then finally documenting the change.
Many of the changes to a system happen through software updates and patches released by a vendor. Therefore, change management processes must address how a company handles patch management. A CCP should work with organizations seeking certification to ensure the configuration management policy addresses patching.
Configuration Management provides recognized, standardized, and established benchmarks that spell out the procedures a company must follow to secure their systems and metrics.
Practices of the Configuration Management Domain
The following security requirements fall under the Configuration Management family:
3.4.1 Establish and maintain baseline configurations and inventories of organization information systems (including hardware, software, firmware, and documentation) throughout the respective system development life cycles.
A company must have a baseline approved by management to meet the assessment objectives under this practice. A CCP will have to work with their clients to ensure the baseline configurations get developed, documented, and maintained for each syetsm. This means identifying all the systems that handle FCI or CUI, monitoring these endpoints, and developing these endpoints so the baseline configuration before meets 171 compliance before user access.
This requires a system development life cycle spelled out in your configuration management plan. You must provide the foundation for the successful development, implementation, and operation of company information systems.
A Certified CMMC Professional has an ethical obligation to include staff on the team, or let who possess security expertise and skills to ensure that needed security capabilities are effectively integrated into configuration management utilizing best practices in reference architecture. Security awareness and training programs can help ensure that individuals having key security roles and responsibilities have the appropriate experience, skills, and expertise to conduct assigned system development life cycle activities. The effective integration of security requirements into enterprise architecture also helps to ensure that important security considerations are addressed early in the system development life cycle and that those considerations are directly related to the company’s business processes. This process also enables the integration of the information security architecture into the enterprise architecture, consistent with company risk management and information security strategies.
The configuration management domain lives and dies based on good document-based artifacts. As a Certified CMMC Professional working with clients to integrate a lifecycle approach you may have to assist clients in developing or curating specifications such as:
- configuration management policy
- procedures addressing the baseline configuration of the information system
- procedures addressing configuration settings for the information system
- configuration management plan
- security plan
- enterprise architecture documentation
- security configuration checklists
- evidence supporting approved deviations from established configuration settings
- change control records
- information system audit records
- information system design documentation
- information system architecture and configuration documentation
- information system configuration settings and associated documentation
- change control records
- other relevant documents or records
The technical members of a Certified CMMC Professional’s team will need to work closely with employees who have configuration management responsibilities, security configuration management responsibilities, and network adminsitrators. Again for many Organizations seeking certification this maybe an IT company or Managed Service Provider with these roles. In this case you must also ensure the shared responsibility matrix or teaming agreements handle baseline configuration, change processes, audit logs, and patching procedures.
A CMMC assessor will want to see these employees or service providers conduct the following tests:
- processes for managing baseline configurations
- automated mechanisms supporting configuration control of the baseline configuration
- processes for managing configuration settings
- automated mechanisms that implement, monitor, and/or control information system configuration settings
- automated mechanisms that identify and/ or document deviations from established configuration settings
3.4.2 Establish and enforce security configuration settings for information technology products employed in organization information systems.
This practice requires companies to bake security into their configuration management plan. A CCP must work with their clients to ensure assets only have features and capabilities that allow them to do their job. A good configuration management policy reflects the most restrictive settings that still allow a business to operate. Like any element of configuration management changes to security tools must get approved, tested, and documented.
Once again a CCP will need to ensure a company has strong document based artifacts to meet the assessment objectives of this practice. These specifications can include:
- configuration management policy
- procedures addressing the baseline configuration of the information system
- procedures addressing configuration settings for the information system
- configuration management plan
- enterprise architecture documentation
- information system design documentation
- information system architecture and configuration documentation
- security configuration checklists
- evidence supporting approved deviations from established configuration settings
- system audit records
- change control records
- other relevant documents or records
A CMMC Assessor will want to see interview the same people and observe many similar tests for this practices as well as other practices in this domain.
3.4.3 Track, review, approve/disapprove, and audit changes to information systems.
To ensure a company meets this practice a Certified CMMC Professional should first identify the IT leadership employees who act as a review board. All changes must get approved an d logged to have enough evidence for the assessment objectives. By building in a set time for the review board to meet you can help clients meet the requirements. You also need to make sure these changes get documents in IT asset management policies.
Numerous changes must get documented. These include modifications to hardware, software, or firmware components and configuration settings. The change process cannot interfere with information system operations. Thus testing needs to reflect company security policies and procedures. They get by information system security policies and procedures default features. Overall a company want to protect the specific health, safety, and environmental risks. Operational systems may need to be taken off-line, or replicated to the extent feasible, before testing can be conducted. If information systems must be taken off-line for testing, the tests are scheduled to occur during planned system outages whenever possible. If testing cannot be conducted on operational systems, organizations employ compensating controls (e.g., testing on replicated systems). Changes to information systems should be reviewed and approved by company management prior to implementation. Beyond the evidence collected for the other practices in this domain a CCP may also want to consider:
- change control records
- information system audit records change control audit and review reports
- agenda /minutes from configuration change control oversight meetings
- other relevant documents or records
Beyond the other individuals interviewed to gather evidence a CCP will want to speak with or help to establish a change review board. A CMMC assessor will want to observe tests on processes for configuration change control and automated mechanisms that implement configuration change control.
3.4.4 Analyze the security impact of changes prior to implementation.
You cannot simply introduce new software and changes to a company’s IT system and information security responsibilities such Information System Administrators, Information System Security Officers, Information System Security Managers, and Information System Security Engineers. Once again for many organizations seeking certification this will involve including external service providers that do IT and security. No one department or person could track the endpoints and software across an entire organization.
When a change gets proposed a process or control board must evaluate the security impact. The review process must have clear testing procedures. Many manufacturers will have a change control board or process as part of their Quality Management System for other certifications such as ISO 9001. A CCP should work with a client, who may not have dedicated IT staff, to meet these requirements using already existing processes. Tracking IT changes using the same process will save companies money and increase security.
A CMMC assessor will want to ensure the effectiveness of theses tests. They must consider if the changes impact compliance with other 171 requirements. All configuration changes should then get tested, validated, and documented on a subset of devices or a staging environment before installing them on the operational system.
This again falls to the importance of the change review board and the importance of clear policy and repeatable procedures with a plan to monitor, meet, and document testing and changes.
3.4.5 Define, document, approve, and enforce physical and logical access restrictions associated with changes to the information system.
Zero trust means little once a malicious or unintentional internal threat has access to your servers and networks. You will need to track and log physical access to key physical areas where changes to the system can get introduced. This will often involve a key card and audit logs. As a CCP work with organizations seeking certification to ensure these areas get clearly marked and penalties for unauthorized access get spelled out in an employee handbook.
For logical access you must consider the implications and how to track who can make security changes to a client’s boundaries. Modern identity management software can require approval, set time bound windows, send notifications to the control board, have role based access and many more features to monitor changes to logical boundaries.
For both physical and logical restrictions always ensure to keep the practices of least privilege in mind.
Beyond the other document-based artifacts already collected for this Domain a CCP must also consider: * logical access approvals * physical access approvals * access credentials * change control records * information system audit records * other relevant documents or records
A CMMC assessor will want to interview employees with logical and physical access. They will need access to employees with information security responsibilities and network administrators.
The assessor will want to see these employees perform automated mechanisms supporting/ implementing/enforcing access restrictions associated with changes to the information system
3.4.6 Employ the principle of least functionality by configuring the information system to provide only essential capabilities.
An employee of a client will not need minesweeper and every Instagram photo filter on their computer in order to do their job. Simply put an Organization Seeking Certification must configure technology so employees only have functions need to keep the system and business operational. A CCP will need to work with a client to identify and remove/disable applications, ports, protocols, services and settings on your systems. This often means imaging machines to remove or add on to default settings.
If a client a CCP works with does not use VOIP than disable the ports VOIP uses.
A CCP will utilize a variety of evidence for document-based artifacts. They should note an inventory of ports gets included in the System Security Plan. ACCMC assessor will want to observe a test on the processes prohibiting or restricting functions, ports, protocols, and/or services
3.4.7 Restrict, disable, and prevent the use of nonessential programs, functions, ports, protocols, and services.
This practice relates closely to 3.4.6, and like many relies on strong IT Asset Management. A company, however, must explicitly define how they limit ports and protocols necessary to provide the service needed for continuation and security. You may disable FTP, for example, or remove applications from a device before access Once again this inventory of ports and programs must get included in the SSP.
In fact companies should consider disabling unused or unnecessary physical and logical ports/ protocols such as Universal Serial Bus (USB), File Transfer Protocol (FTP), and Hyper Text Transfer Protocol (HTTP on information systems to prevent unauthorized connectios As a CCP you may have to help an organization seeking certification evaluate companies that can utilize network scanning tools, intrusion detection and prevention systems, and end-point protections. Firewalls and host-based intrusion detection systems to identify and prevent the use of prohibited functions, ports, protocols, and services can also help mitigate much risk. As a CCP help clients gather evidence from typical document-based artifacts that include.
- configuration management policy
- procedures addressing least functionality in the information system
- configuration management plan
- security plan
- nformation system design documentation
- information system configuration settings and associated documentation
- specifications for preventing software program execution
- security configuration checklists
- documented reviews of functions, ports, protocols, and/or services
- change control records
- information system audit records
- other relevant documents or records
A Certified CMMC Professional will need to work with employees with responsibilities for reviewing functions, ports, protocols, and services on the information system and network administrators. Together make sure observable test can get performed on:
- processes for reviewing/disabling non-secure functions, ports, protocols, and/or services
- automated mechanisms implementing review and disabling of non-secure functions, ports, protocols, and/or services
- processes preventing program execution on the information system
- processes for software program usage and restrictions
- automated mechanisms preventing program execution on the information system
- automated mechanisms supporting and/or implementing software program usage and restrictions
3.4.8 Apply deny-by-exception (blacklist) policy to prevent the use of unauthorized software or deny-all, permit-by-exception (whitelisting policy to allow the execution of authorized software.
This practice builds on top 3.4.7 but requires companies to maintain a list of approved software and a list of software denied to all or requiring an exception. In fact many organizations go beyond the minum of this control and organizations verifying the integrity of approve-listed software programs usingcryptographic checksums, digital signatures, or hash functions. These certificates help to verify versions and secure updates.
Between maintaining an approved list and a not-authorized list, the denial list provides stronger protection. Policies alos get deployed to prevent certain types of software from being run on the company’s systems such as games. A CCP will need to ensure a client checks these policies s by periodic audit.
Beyond the usual document based artifacts of this domain a CCP will want to help an organization seeking certification organize evidence from:
- information system configuration settings and associated documentation
- list of software programs not authorized to execute on the information system
- list of software programs authorized to execute on the information system
- security configuration checklists
- review and update records associated with list of unauthorized software programs
- review and update records associated with list of authorized software programs
- change control records
Employees with information security responsibilities and network administrators will need to know how to demonstrate tests on
- process for identifying, reviewing, and updating programs not authorized to execute on the information system
- process for identifying, reviewing, and updating programs authorized to execute on the information system
- process for implementing blacklisting automated mechanisms supporting and/or implementing blacklisting
- process for implementing whitelisting automated mechanisms supporting and/or implementing whitelisting
3.4.9 Control and monitor user-installed software.
As a Certified CMMC professional just make sure companies disable user installed software on in scope systems. Remember users should not have privileged or admin access on machines that connect to your network and all privileged users always require MFA authentication. This will allow a company to control unapproved software.
Policies must fully describe allowed installations and procedures to check that for policy violations. These polices may want to have very stringent exceptions for installing software, especially on the devices of privileged users.
A CMMC Assessor will not only want to review these policies and procedures but they will want to see employees perform tests on processes governing user-installed software on the information system an automated mechanisms for alerting personnel/roles when unauthorized installation of software gets detected.
If a company takes the time to put down a clear pathway for configuration management we can help to protect the confidentiality of information. Just remember while we need to get to the finish line one should approach it more as conditioning. Once you have your baseline configured get back to tthe starting line and review the deployment as you maintiain the overall cyber health of a company.
“Starting Line” by Phil Roeder flickr.com/photos/ta… is licensed under CC BY
-
Attending the John Ellis Talk on CMMC 2.0 hosted by PrVeil
-
Overview of CMMC 2.0
Ben Franklin once quipped, ““When you are finished changing, you are finished.”
Nothing could ring more true in cybersecurity. Frameworks need to live and breath to respond to evolving threats.
On November 4, 2021 the Department of Defense unveiled an update to the the Cybersecurity Maturity Model Certification framework to streamline compliance, increase flexibility, and lower cost for manufacturers and IT providers.
TLDR
- Reduce number of levels from Five to Three
- Return to NIST as maintainer of all documents
- Allow level one self-assessments
- Self-assessments require senior level affirmation
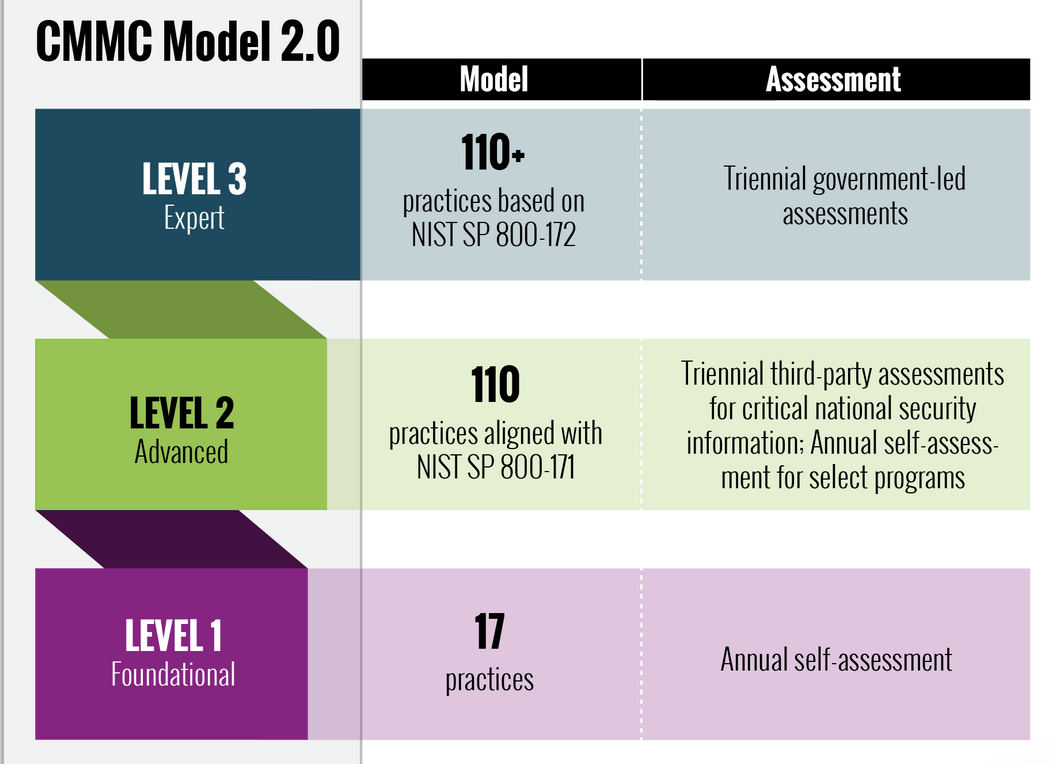
- Level Two is Old Level Three and NIST SP800-171 baseline for Controlled Unclassified Information
- Level Two is bifurcated into priortized and non-prioritized contracts
- Prioritized contracts require third party assessments.
- Return of limited time bound POAMS
- Return of limited approved waivers
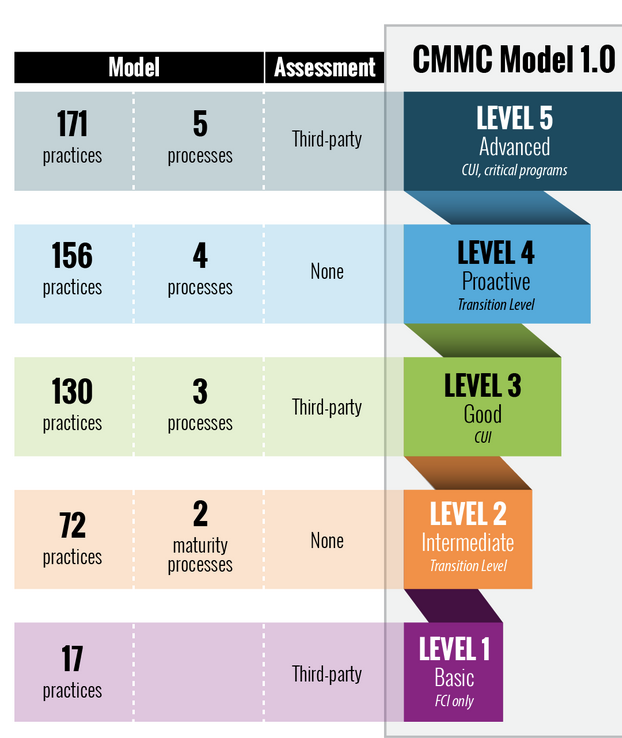
Reduced Levels
CMMC 1.0 had five levels. Level One aligned to seventeen controls from NIST SP-800-171 to meet the fifteen safeguards required by FAR 52.204.21 for Federal Contract Information. Level Three, required for CUI, aligned to 110 controls from NIST SP-800-171 and 20 additional controls. Level Five would align to practices selected from NIST SP-800-172.
This model did not work for maturity given the different baselines required for sensitive data. One would not seek a level two certification. In fact, DoD said no bids would even ask for a level two. We also had no classes or assessments for level two or four.
Yet CMMC 1.0 had cummulative levels. Meaning you had to meet all of level one and two to meet level three. This pushed some CUI requirements down to level two which made no sense given lvel three served as the NIST SP-800-171 baseline.
CMMC 2.0 removes the ill-fitted maturity requirements.
Return of National Institute of Standards and Technology
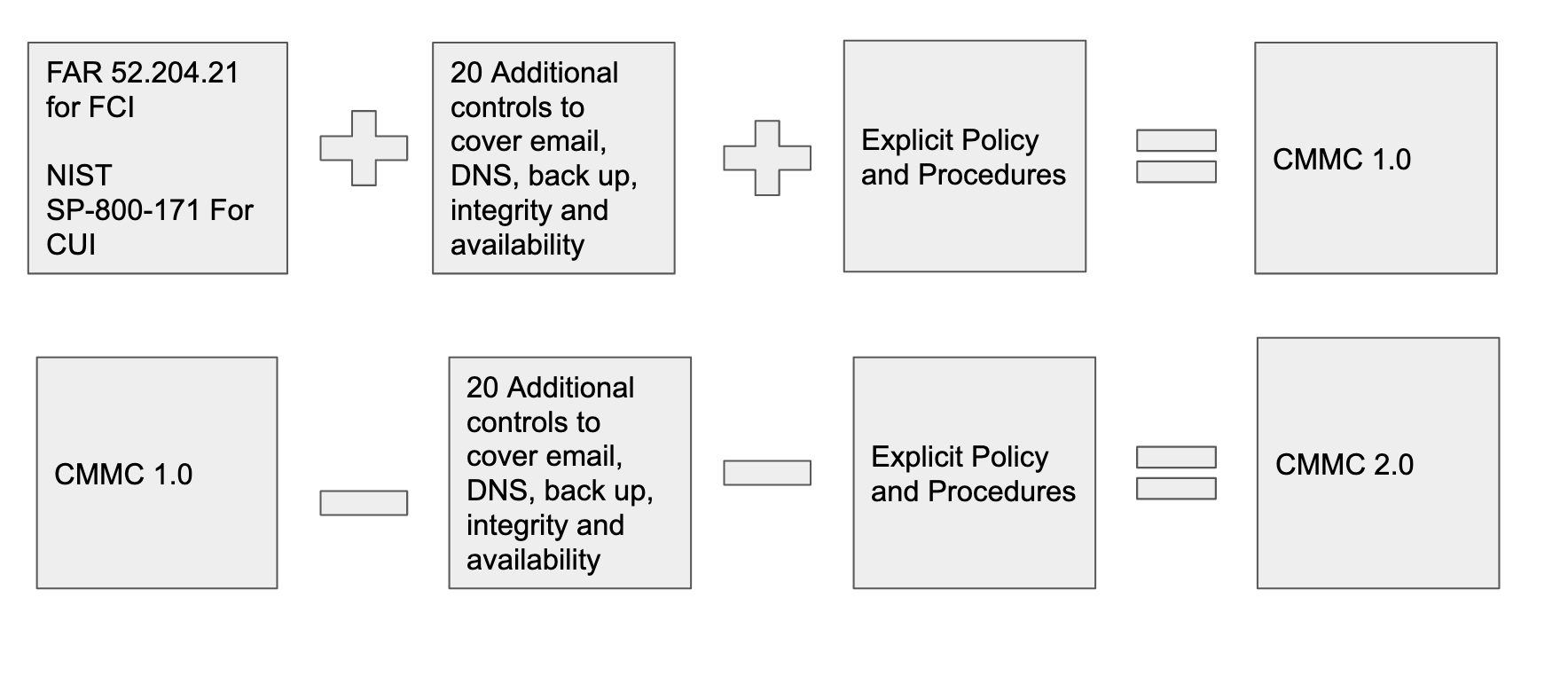
CMMC 1.0 tried to address some of the shortcomings of NIST-SP-800-171. In fact, early on the AB, rumor has it, tried to remove requirements until NARA/ISOO reminded them that the CUI program exists in law and NIST-SP-800-171 provides the baseline. They could only add and not remove.
CMMC 1.0 added twenty additional practices, often referred to the Delta 20s, and made the assumed controls of NIST-SP-800-171 around policy and procedures (an assumption of practices Non Federal Organizations (NFO) just do..they don’t) explict in the process maturity measures.
CMMC 2.0 removes anything unique to CMMC and returns us to just NIST-SP-800-171. Moving forward only NIST will change the requirements. We will see many of the delta 20s making a return, and while policies and procedures do not get explicitly assessed you can not pass an assessment without policy and procedures.
Timeline and Rulemaking
In order to allow for third party assessments under the Defense Federal Acquisition Supplemental regulations the Department of Defense (more likely their lawyers) decided we need to codify this in federal law.
This requires a “harmonization” of rulemaking. First CFR 32, which governs the CUI program needs revision. Then CFR 48, which enables DFARS will get revised.
Federal rule making takes a long time and the DoD estimates suggest 9-24 months. Before contractors breath a sigh of relief they should realize that a 24 month timeframe speeds up the original intent of the five year pilot program.
Once the rule making process gets complete no pilot program will get unrolled because compliance with 171 required since 2017. The rule changing just empowers third party assessments under the DFARS clauses.
More Flexibility
CMMC 1.0 did not allow for any open assessment objectives. You had to meet all 305 to get a level three certification.
CMMC 2.0 allows for a set of limited and timebound POAMs.
Before you jump for joy and think you can couch really expensive stuff as an ever ending POA with a never reached milestones you should understand the caveats.
First you need a minimum SPRS score self-assessing or having a third party assess you against the 171a methodology. A cut score still exists. They have lowered the threshold. How far? We do not know, but it won’t be low.
You also can not POAM all the requirements and objectives. 171a breaks scores down into 5, 3, or 1. While official guidance did not get released officials have hinted no five pointers in the POAM. The most expensive stuff gets five points.
You also get 180 days to rectify the POAM. This flexibility saves you nothing. In fact trying to address a five point control in three months may cost you a ton more than good planning.
What does it Mean?
For organizations seeking certification, little. Keep growing the SSP and shrinking the POAM. We always had 171 as a baseline and that did not change. The Interim DFARS clauses 7019 and 7020 did not go away. DFARS clause 7012 did not go away. If you have CUI or FCI on your systems the people, processes, and technology within scope still fall in scope.
For CEO or CIO of organization seeking certification the affirmation requirements increase your personal liability under Fair Clause Claim. In fact both the DoJ and the DoD have highlighted increased focused on the whistleblower elements of the Fair Claims Act. You may find your lawyers, or more likely your Prime’s lawyers demanding a third-party assessment even if you do not hold CUI on a prioritized contract.
Nobody knows what prioritized contracts mean. You cannot plan on what level of level two you will fall under. Plan your self-assessment as if a third-party assessor will come in and verify your results.
If you wanted to join the ecosystem as a Certified CMMC Professional CCP or a CMMC Certified Assessor you may find the market grew instead of the logical conclusion the market contracted with self-assessments.
It makes sense for the DoD to press pause on third party assessments. They have no idea how big the DIB is but they knew the majority would fail a level one, forget a level three assessment. Why make companies pay for a test you know they will fail?
Yet the market for CCPs and CCAs may have grown. While the DoD may not require a third-party assessor you can bet many a Prime contractor will if you want to remain in their supply chain. Further the number of companies who need to self-assess will require more support.
The number of companies needing a third party assessor remains high. The DoD has pinned this number on 30,000-40,000 and the CMMC-AB places it higher. Further, current thinking, likely to change, has any level three company who wants an assessment by the Government against the upcoming tailored controls from 172 must first have a level two assessment from a C3PAO against 171.
In the end, the baseline of NIST-SP-800-171 did not change. Use the next nine to 24 months to grow the SSP and shrink the POAM.
Change flickr photo by Matt Henry photos shared under a Creative Commons (BY) license
-
No CMMC Hot Takes. Just Take the Time for Some Slow Reads

Inbox overflowing with email invitations to CMMC.20 webinars? Every consultant and software service promising to give you the most up to date info your company can not do without?
You can do without. I offer no hot takes.
Just some slow reads.
If you really want to get prepared start reading. Congress got it wrong. Cybersecurity does take reading. A ton of reading.
We know CMMC 2.0 will not kick in for 9-24 months on government clocks. I have no idea how long that will last in real time or dog years.
Until then read.
Evaluate the System Security Plan (SSP).
Read more.
Throw out your poorly templated SSP and start over.
Read more.
Finalize the SSP and write your POAM.
Read more.
Have set meetings to address POAM. Revist SSP in six months.
Read more.
Grow the SSP and Shrink the POAM.
If you do not want to do the reading hire an expert. You can try to do cybersecurity without reading. You can also try accounting without math.
So instead of beating you over the head with one more CMMC 2.0 webinar I offer you my top ten hit reading list for 7012 compliance.
Reading and Time. My turnkey easy button solution to CMMC 2.0
- FIPS-199/200 - The basic controls. Only thing gov truly mandates
- SP 800-30 and 39 -learn the risk management process
- SP 800-37 - Do risk management
- SP 800-18 - How to write an SSP
- SP 800-60 & 70 - Mapping data flows and info system
- SP 800-53 - 1200 controls in the catalog. Spend a hot minute here.
- SP -800-171 -Learn the derived controls selected from 53 that combined with the basic controls from FIPS that you must have on nonfederal system (don’t skip Appendices)
- SP 800-115 - How do we test controls 9 SP 800-162 How to speak engineer to humans
- SP 800-137 - continuous monitoring guideline
Bonus reading: SP 800-161 Supply chain risk management
img credit: “A Shot of Ice and Fire” by ElleFlorio flickr.com/photos/el… is licensed under CC BY-SA
-
When Did Small Businesses Become the Enemy of Cybersecurity?

When did growth become evil in America?
When did we start believing the Government can handle complex and quickly shifting problem spaces with an agility the private sector cannot match? When did we start rooting against cottage industries?
When did the entrepreneur become the enemy?
According to critics of the Cybersecurity Maturity Model Certification program small businesses became a threat when the Defense Department tried to set up a system to upskill small manufacturers through third party assessments.
CMMC 2.0 and Fear of Cottage Industries
I lament the number of people who have cheered the Department of Defense shutting down what may have led to the largest cybersecurity training in our Nation’s history (still pales in comparison to the investment China makes in their workforce).
You read blog post after blog post cheering the “shuttering of the CMMC cottage industry” or those snickering at C3PAOs who expected a market cap between 100-300,000 companies see hundreds of thousands in investments shrivel on the vine of time we call federal rule making.
We, as a nation, through the efforts to scale CMMC could have addressed critical pipeline issues in IT, cybersecurity, machine learning, and artificial intelligence.
Little ole me, nothing but a former middle school teacher with a blog, could even use CMMC 1.0 to build a massive network. I have four universities, Southern Connecticut State University, Capitol Technology University, Emory University, and Metropolitan State University of Denver delivering LTP curriculum. My University, SCSU, has even proposed a 171/CMMC pathway into our Cybersecurity Master’s program which works it’s way through Shared Governance.
The support DoD decided to give in creating a CMMC vertical for 171 assessments would have also helped us address diversity, equity, and inclusion. Many of the schools involved offered free CMMC class tuition to their students. At my school, and many in the network, People of Color make up most of the student body. The opposite is true in the cyber industry.
We were even working with high schools and states, specifically CT and SC, on a 2x2x2 apprenticeship. program. Students would earn IT and networking certs starting their junior year and high school, do internships and graduate with a CCP, they would then enroll two years in a community college and get paid internships while earning other certs and a CCA1, then transferring to a four year institution for two years to get a degree in cyber, have more paid apprenticeships, and leave a CCA3.
Community groups about CMMC sprouted up across the country. I helped to found the CT CMMC Coalition, soon Northeast CMMC Coalition, which we will incorporate into a member owned co-op. We have released 100s of openly licensed pages of contents LPPs use for free in their training. The CMMC Info Institute provides another great example of a non-profit in this space. Their webinars have taught hundreds.
All of this can go away if the naysayers win. CMMC 2.0 rolled the clock back to 2017 and drastically reduced the need for third party assessors. Feels like we decided to fit the mission to the weapons we have rather than get our hands dirty and build the weapons the mission needs.
Cottage industries do not represent a threat to National Security. They provide a Mannerheim Line against a modern battle space. I fear with CMMC 2.0 the DoD has decided to comfortably wait things out behind the Maginot line of self-assessment.
DoD Should Support Cyber Businesses
I hear from the cottage industry critics that supporting small businesses detracts from DoD’s mission and they don’t do economic development. Then why does Farooq Mitha Direct the Defense Department’s office of small business programs? Why do we have Procurement Technical Assistance Centers? Why does every branch of the military give out billions annually in small business grants through SBIR/STTR?
CMMC 1.0, in two years, accomplished more growth in the GovCon cyber sector than all past efforts combined. The Defense department did this while spending next to nothing and issuing a no cost contract to the CMMC-AB.
Growth in the sector will take more than Project Spectrum, and small business efforts in the Defense Department need to transition from just supporting kinetic efforts and start investing in our cyber workforce.
##Headcount Issues Threaten Our Nation
You think finding headcount difficult now? Just wait until the Portman/Peters FISMA reauthorization passes and every federal department must conduct ongoing pen testing. Trust me, I help fill the seats, cleared pentesters do not grow on trees. Have you counted the amount of funding CISA will get from the infrastructure bill and pending cyber bill. Hundreds of billons. Where will we find the people?
CMMC 1.0 could have provided the pipeline if the market could have gotten established.
Instead, folks found it more American to cheer against small businesses. They jeered at the Department of Defense desire to support small assessment companies in a nascent cottage industry. Critics demanded we roll back the clocks to 2017 and erase CMMC 1.0. Naysayers want the government and not private industry to help secure and assess cyber and IT in our manufacturing base.
I disagree, and to all those who dream of starting a cottage industry I salute you.
img credit: “Engineering Shed” by Tim Sheerman-Chase flickr.com/photos/ti… is licensed under CC BY
-
Cybersecurity: Did Bootcamps Break Us or Save Us

The cybersecurity awareness and training industry tops a billion dollars in revenue and will only grow as regulatory frameworks that require companywide learning programs spread.
At the same time and given Higher Education’s inability to adapt or keep up in digital fields, a training program that tops hundreds of billions of dollars grew overnight. In fact, a study by CompTIA (bias disclosure: a test vendor) found 91% of all employees use certifications in hiring.
Classes to pass the certification exploded overnight. I worry the bootcamp model broke us.
I do not want people equating a four-day class in how to pass a test to equal deep learning based in cognitive science. Not when it comes to cybersecurity. The mission too important to hunt for a quick fix in awareness and training.
I know, like CMMC these certification classes are not meant to teach cybersecurity skills. Still, I personally believe the domains of knowledge assessed on the certified classes too hard to master in a four-day seminar.
I don’t blame anyone, but human nature. You can never lay shame on someone for taking the path of least resistance when it comes to securing food or shelter for them and theirs. Once you introduce a high stakes test humans will immediately start mixing a broth to corrupt the reliability and validity of that test.
At the same time these increased cost and regulations caused expected resentment in the cybersecurity professional community. Many feel their experience has established these skills and they feel preyed upon by a certificate mill industry. They have a point.
The entire tech industry, however (I included) could benefit from a good dose of humility. Nobody knows it all, and if you know more, others in the class benefit. Those most successful in bootcamp classes are probably humble folks in other online spaces.
Bootcamp Model
In a “bootcamp” style class, whether to train employees or to prepare for a certification test ,the learning gets crammed into a very short time frame over long extended days.
Almost all cognitive science research supports longer durations for learning. In fact, retention ability decays very quickly. Further long-term transfer to other domains increases when high quality feedback gets connected with bursts of content, activity, and reflection.
Bootcamp models do work, and we have emerging research to support this, in well-defined domains with discrete skill sets. Configuring your endpoint detection, learning to write JavaScript, even playing Clarinet.
The Domain of cybersecurity, especially when preparing to move from one industry framework or another, however, cannot happen overnight. Yes, as I stated these classes do not train you in cybersecurity, but it will take specialized knowledge to move from a HIPPA audit to a 171 assessment for example.
These domains of knowledge too complex for quick learning just to check off a compliance box.
Myth of Auto-Didactic Learner
No bootcamp lives in a vacuum (until Space Force starts orbital unit training) so when people claim to only want self-paced learning, they should make sure they have community support somewhere.
Nobody learns alone. No one gets self-taught. Full stop.
Community is the Curriculum.
The original MOOCS, which helped kick off the coding and cybersecurity bootcamp craze, never focused on size. they focused on people. When David Cormier coined the term the massive modified open, not the size of the class.
It meant using network theory to encourage the spread of open resources and pedagogy through ever growing learning communities.
So even a four day or four-week self-paced online class needs some element of community. You need peers to have discussions. You need groups to work on scenarios and case studies that will reflect what cybersecurity and assessors will do in the field. Most importantly you need high quality feedback from your instructors.
Not opinion. Stable and replicable finding from cognitive science research and based on principles of Universal Design for Learning to ensure all learners can succeed.
Bootcamp Models Dont Meet Diverse Workforce Needs
You need a lot of resources to check out for four days and go to an intensive bootcamp. Childcare, carpools, community volunteering, the bootcamp model do not reflect the needs of the modern workforce.
Bootcamp models do not help diversity, equity, and inclusion when the only option involves four days of unpaid work. We need to provide learning communities that allow for flexible and supportive learning modalities. As a nation we must root cybersecurity trainings in groups that face historical exclusion in the tech and cyber industry.
These four-day learning bonanzas also hurt organizations. As a CEO do you want your entire cyber/IT team out of pocket for four days? What if like many small businesses as CEO you are your entire cyber/IT team? Can you be out for four days?
A Better Way forward with CyberDI and Southern Connecticut State University
At SCSU, we have developed and iterated on the CyberDI curriculum that they will deliver on our online and offline campuses as an LTP through four rounds of iterative design with the goals of using principles of cognitive science in curriculum development and delivery.
Real science. Not bootcamp marketing or certificate mill hype.
In our five-week class model you meet twice a week for live classes each week. Instructors schedules these classes either at noon, the evening, or the weekends depending on local audience needs. They offer hybrid and fully online versions. The lectures and discussions get recorded so if life gets in the way anyone can catch up.
Every practice and process in the CMMC model gets covered through systematic and explicit instruction following the “Instructor does, class does, you do” model. This predictability, science tells, us, improves learning.
Social learning, not just explicit instruction, gets baked into the model. We have two weekly office hours where instructors and community members just drop in to get specific technical help or to ask general questions about course content.
We know from research, building scaffolds that gives learners support drives success.
Our course navigation is simple and works in Blackboard, Canva, Microsoft Teams, or my favorite a simple HTML website. In every module you are asked to read, write, and participate. We give you access to easy to navigate resources.
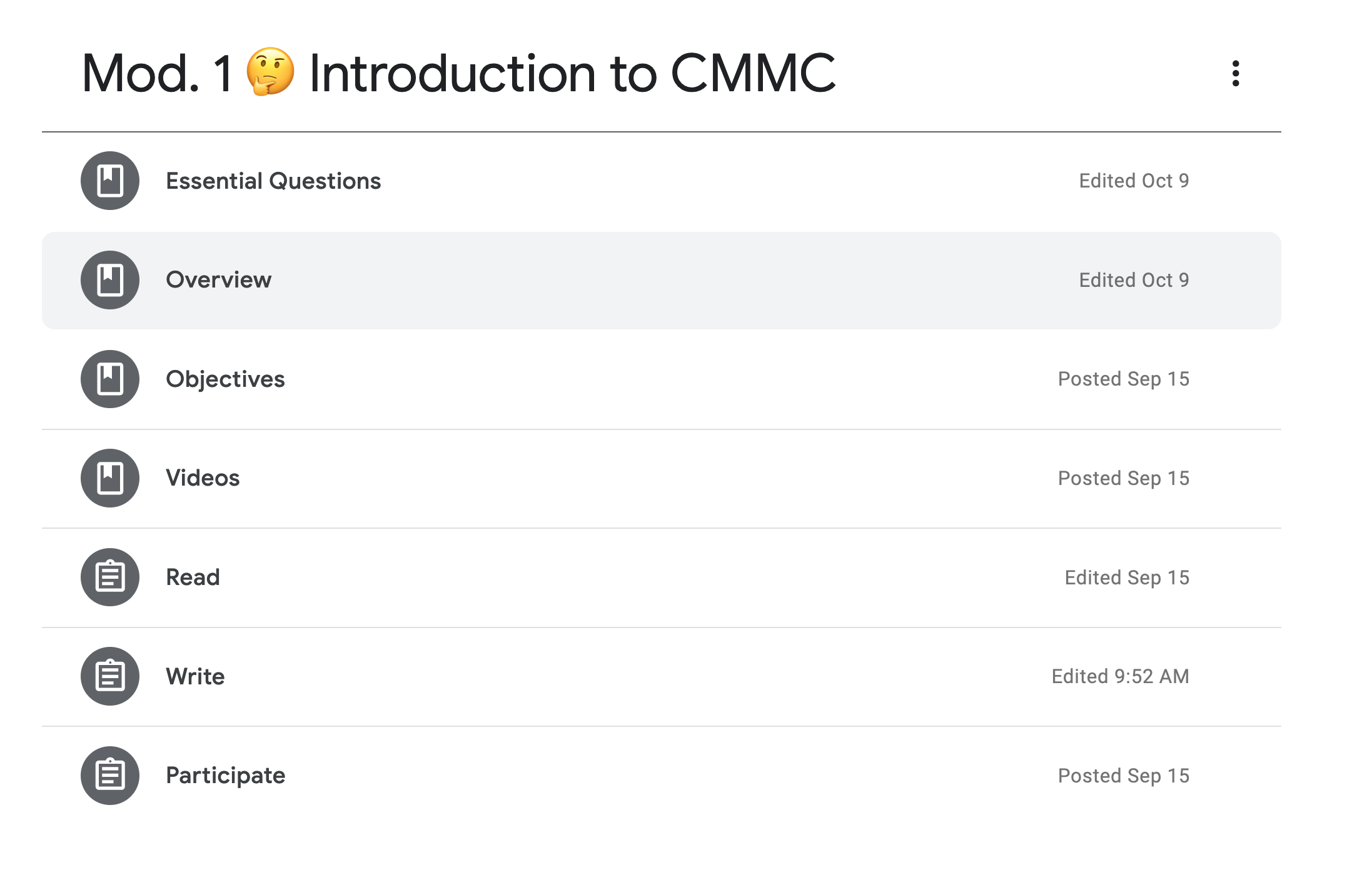
You can see above how each model gets laid out in a Google Classroom example. We know from decades of research ease of navigation drives learner efficacy and success.
Most importantly you take part in production-based learning driven by feedback designed to elicit growth against the course objectives. Feedback, both formal and informal, drive learning. The teacher guide we provide has tips on writing feedback. The instructors who teach the CyberDI classes on SCSU campuses will get on going coaching in their questioning and discussion techniques. They get additional training on how to write and deliver feedback for growth.
We do hope you choose a training program based in cognitive science and not just certificate mill marketing hype. The classes CyberDI will teach on our campuses meet this criteria.
Just wanted to end with a quick shoutout to the subject experts who helped write and shape the curriculum
Curriculum Authors:
- Leighton Johnson- Wrote our Domain Scenarios
- Paul Netopski- Wrote our CMMC Assessment Process Chapter
- Vincent Scott- Co-wrote history of CMMC and Domain Scenarios
- Tom Cornelius- Open Source contributor. We utilize Comp;iance Forge’s CC BY-SA Scoping Guidance.
- Gregory McVerry co-wrote CUI scenarios, co-edited textbook with Dr. Tucker
- Lauren Tucker-lead author on instructinal guide, co-edited text book
- Richard Dawson-Wrote 162 aligned introductions for 17 Comains
- Dana Mantilla-Video Instructor who interviewed top talent
- Brian Rogalski-co-wrote CUI scenarios
Academic Advisor: Leslie Weinstein
Video Guests:
- Allison Giddens
- Vincent Scott
- Margaret Glover
- Paul Netopski
- Matthew Carson
- Jake Williams
- Amira Armond
- Ryan Heildron
- Vic Malloy
- Kyle Lai
img credit: Bootcamp dreams. by jgmac1106 shared under an CC-BY-SA license a A remix of: Work boot” by Bigbadvoo flickr.com/photos/bi… is licensed under CC BY “Storm Clouds Gathering” by izoo3y flickr.com/photos/iz… is licensed under CC BY-SA “Cha-Ching” by spcbrass flickr.com/photos/sp… is licensed under CC BY-SA
-
How to Register on the CMMC-AB Class to Sign up for a CCP Class with an LTP
Wow that title has a lot of letters. Luckily the registration process on the Cybersecurity Maturity Model Certification Accreditation Board website to create an account so you can sign up for a Certified CMMC Professional class with a Licensed Training Provider is not as difficult.
Creating a profile on to register for a Certified CMMC Professional course requires a three-step process and a $200 fee paid to the CMMC Accreditation Board and not the Licensed Training Partner. The fee also does not cover the CCP exam. That will cost an additional $275.00
You must first create an account on the CMMC-AB Moodle page (yeah open source).
Once you do you a verification email gets sent your inbox
After you verify your email you choose an MFA, multifactor authorization, method.
Depending on which method you chose you may have additional security checks
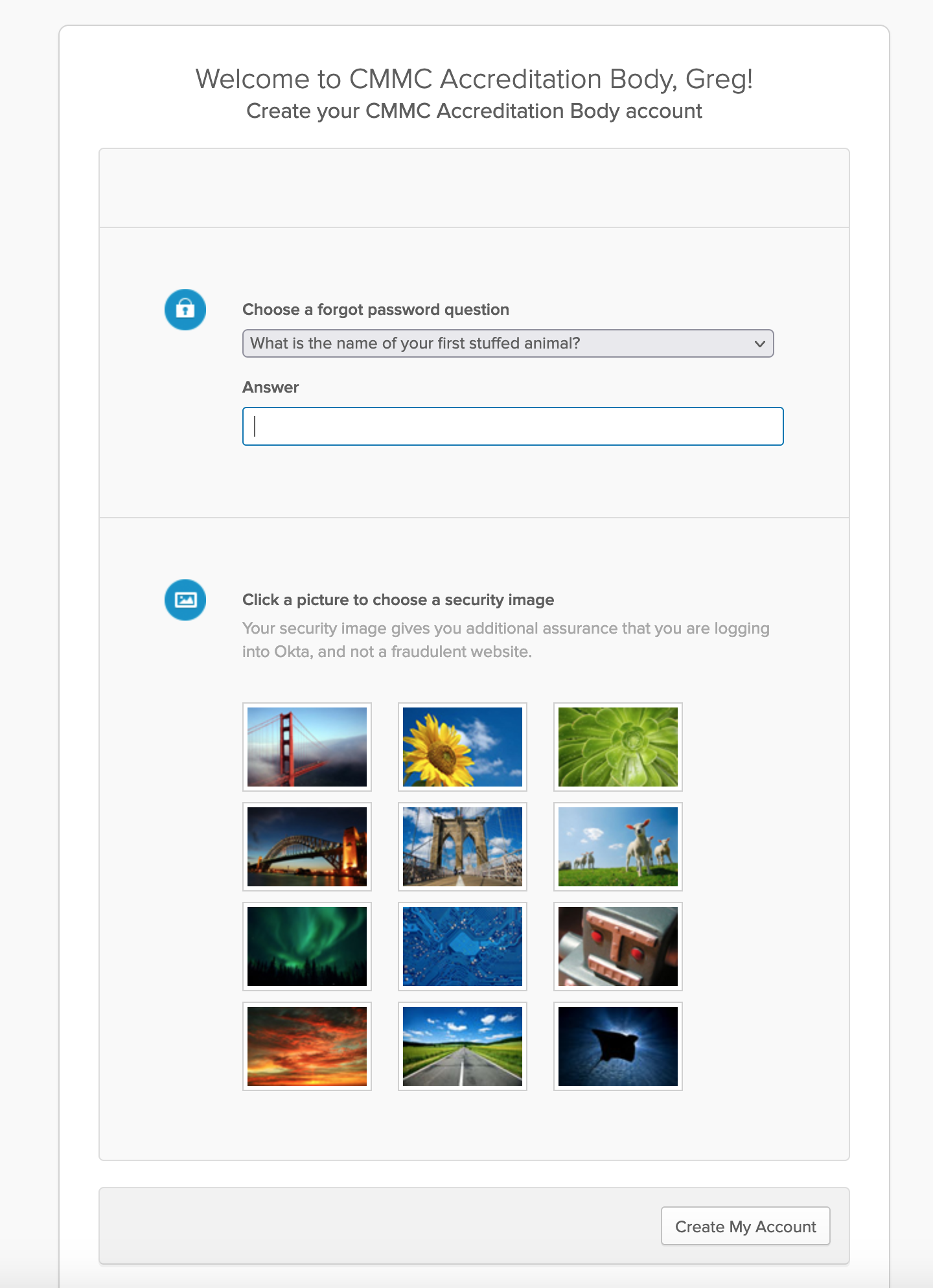
Once you have an account you can move on to Step One which requires you to make a profile
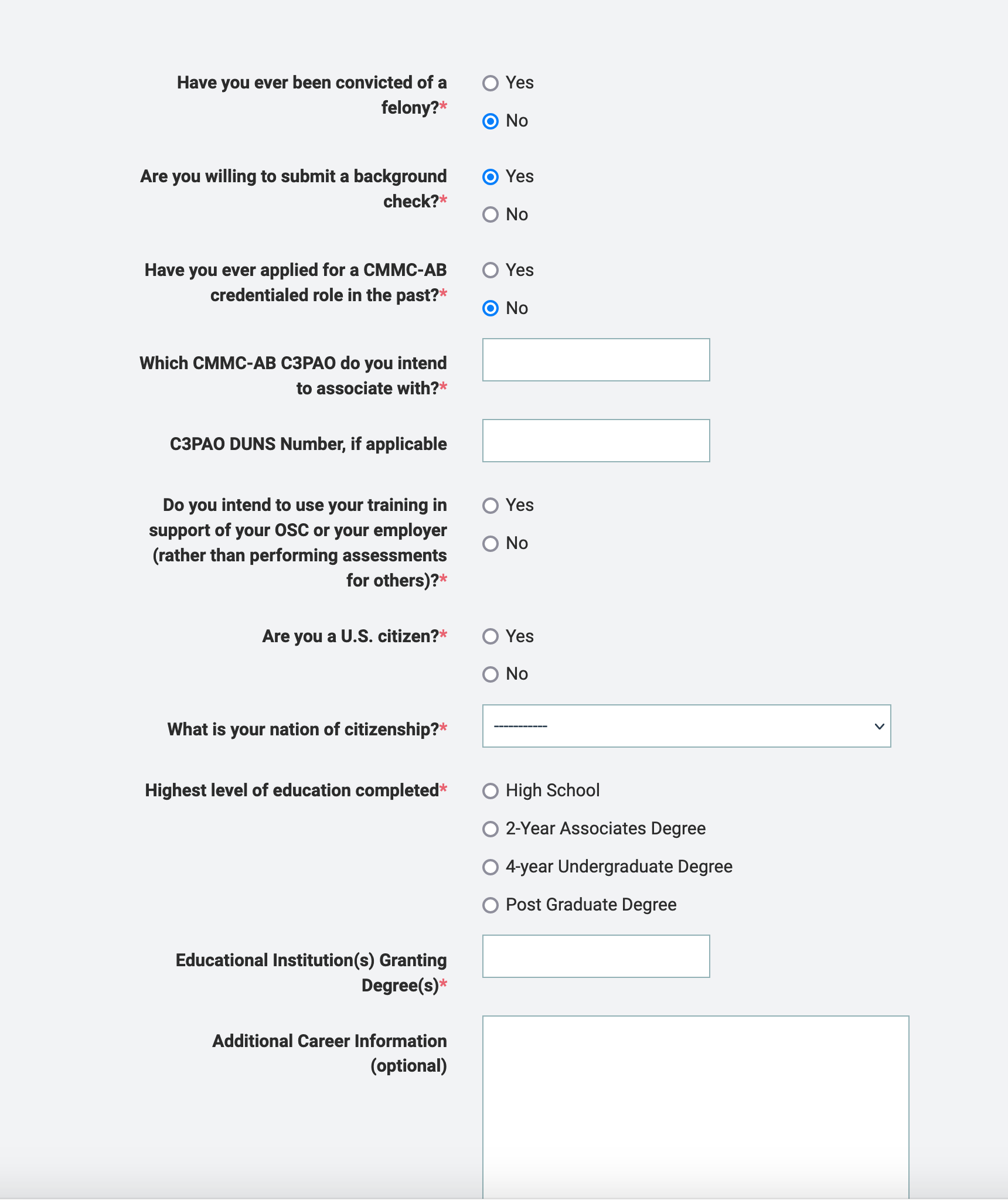
Once you make the profile you can then go and register for the CCP class. The application is extensive. You will upload your resume and any certifications you hold.
The application did ask me to associate with a C3PAO. Currently, as far as I know, the CCP does not need to associate with a C3PAO. I put “none yet” and my application went through.
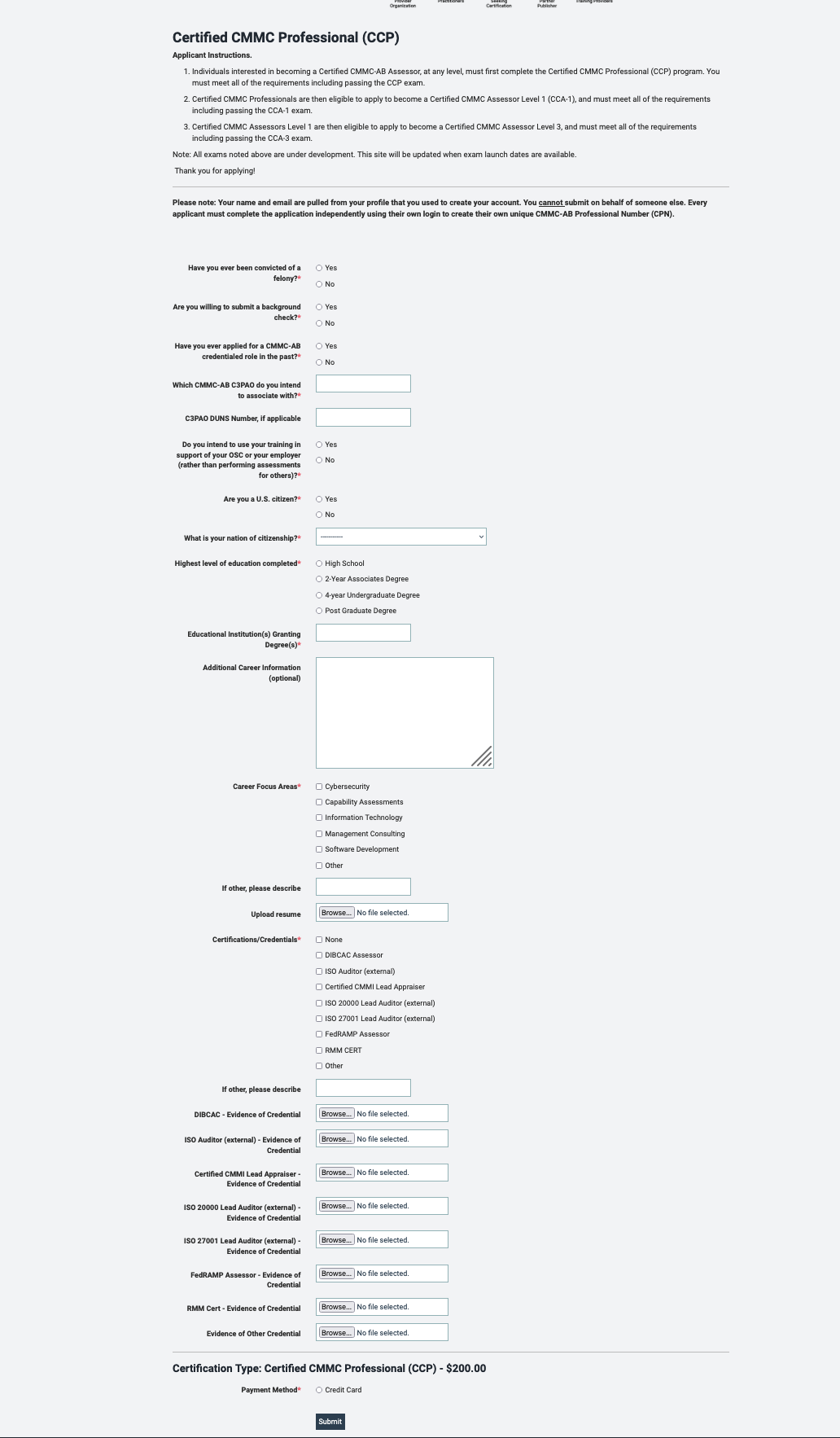
Pay the money and you can now register for a class with an LTP.
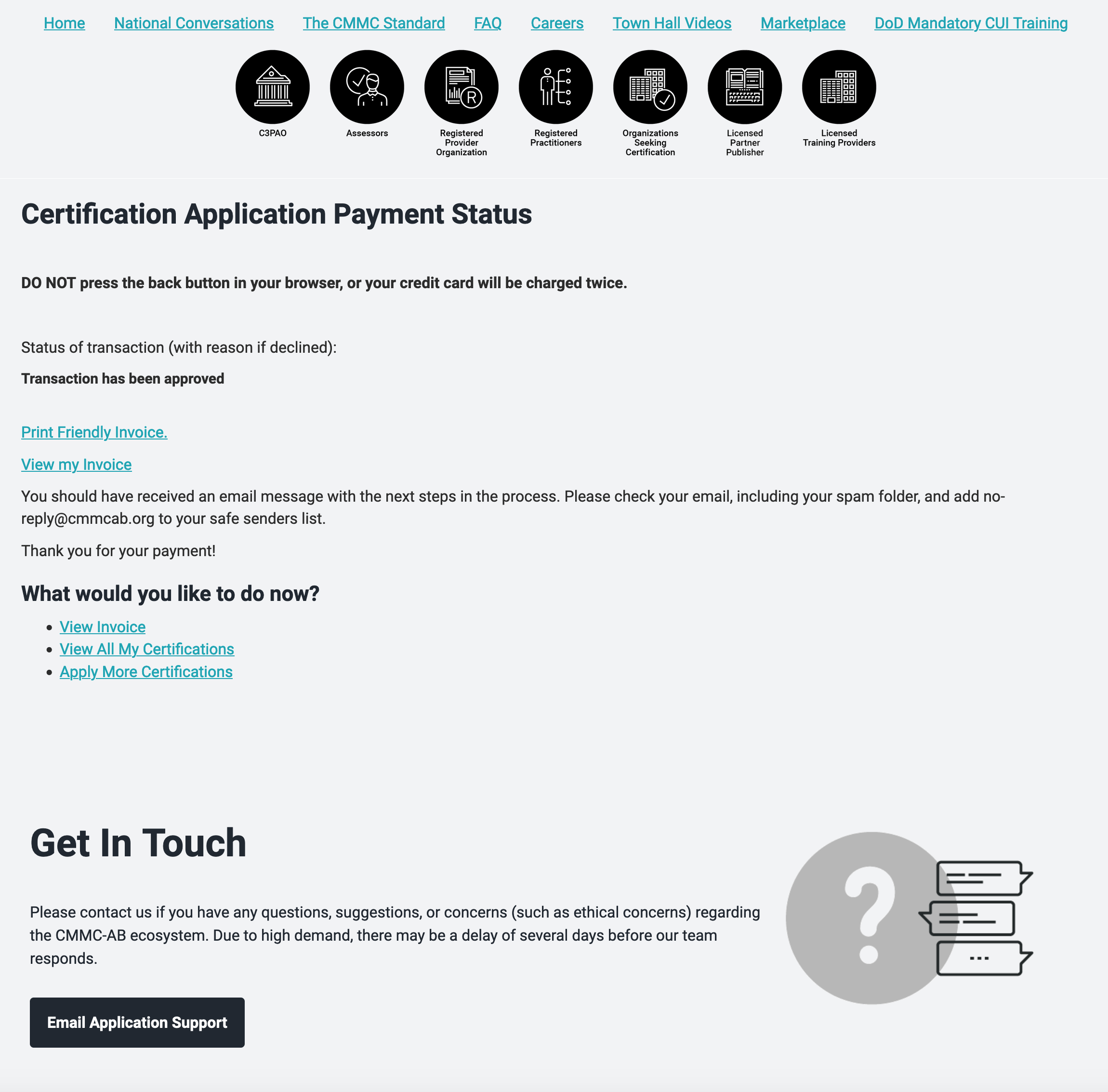
You will get an ID number. The LTP will use this to share your progress and enrollment status.
-




-

We want to transform CyberSecurity Awareness and Training into an active learning process. For far too long we have assumed video-based quizzes work at the minimum and real training cannot happen because you need decades of experience to do Cyber.
Neither assumption rings true. Active learning leads to greater transfer and retention. This production-based method, where learners must do stuff with what they learn begins with questioning.
In my time working on Cybersecurity Maturity Model Certification courses, I have reviewed so much curriculum. Coched Provisional Instructors as they develop lesson plans and provided feedback to our instructors as we iterate on curriculum at Southern Connecticut State University.
Stop Asking Any Questions
Almost all the instruction I observe relies on direct intruction with little learner interaction. I see it in video based training and lectures where a highly talented Subject Matter Expers asks, “Any Questions” at the end of each segment or lecture.
Everyone has questions. No one will ask.
Instead a good teacher uses questions to elicit evidence of and scaffold knowledge growth. You can think of three types
- Literal
- Inferential
- Evaluative
Literal questions get answered with explicit, which means identifiable in the text, details. Inferential questions require students to combine information in a text, either explicitly or implied, and combine this with prior knowledge or another source. Evaluative questions ask you to combine implicit information with an opinion and may focus on why and how to fill is missing details.
As an instructor you need to plan your questioning well. You can use verbs from Bloom’s Taxonomy or Webb’s Depth of Knowledge, but you need to ask questions for learning to occur.
Helping Out CMMC Instructors
So, to help out the Instructors who utilize the CMMC curriculum we write we started to create a question guide for each of the 17 Domains. It includes a definition from NIST SP-800-162 and questions a Certified CMMC Professional can use to help an Organization Seeking Certification. We derive these from 162 as well.
We then include every assessment objective. CMMC courses mean nothing without Assessment Objectives. Next, we close with sample discussion questions. We hope these focus on pain points and common misconceptions. When an LTP or Provisional Instructor uses our material, you can know we provide you the tools to have active discussions,
Check out our Access Control Example
Featured Image “Question” by kevin dooley is licensed under CC BY
-
Writing threat scenarios.
-
What does the NDAA say About CMMC?

The NDAA goes deep into developing the Cyber Director role but for those looking to NDAA for “significant changes” to the cybersecurity maturity model certification (CMMC) program should look elsewhere.
There are eight mentions of CMMC in the bill. I will need to dissect the fund allocations to CMMC. There are an additional five mentions of the cybersecurity maturity model certification in areas of threat and incident response.
It looks like the House Small Business Committee that complained about contractors “having to read really big books” did not have their ammendment approved.
It is really just section 1742 of the bill.
IN GENERAL.—Not later than March 1, 2021, the Sec- retary of Defense, acting through the Chief Information Officer of the Department of Defense and the Commander, Joint Forces Headquarters-Department of Defense Information Network, shall assess each Department component against the Cyberse- curity Maturity Model Certification (CMMC) framework and submit to the congressional defense committees a report that identifies each such component’s CMMC level and implementa- tion of the cybersecurity practices and capabilities required in each of the levels of the CMMC framework.
The report shall shall include, for each component that does not achieve at least level 3 status (referred to as ‘‘good cyber hygiene’’ in CMMC Model ver. 1.02), a determination as to whether and details as to how— (A) such component will implement relevant security measures to achieve a desired CMMC or other appropriate capability and performance threshold prior to March 1, 2022; and (B) such component will mitigate potential risks until such measures are implemented. (2) COMPTROLLER GENERAL REPORT REQUIRED.—Not later than 180 days after the submission of the report required under paragraph (1), the Comptroller General of the United States shall conduct an independent review of the report and provide a briefing to the congressional defense committees on the findings of the review.
CYBERSECURITY MATURITY MODEL CERTIFICATION FUNDING LIMITATION.—Of the funds authorized to be appropriated by this Act for fiscal year 2021 for implementation of the CMMC, not more than 60 percent of such funds may be obligated or expended until the Under Secretary of Defense for Acquisition and Sustainment delivers to the congressional defense committees a plan for implementation of the CMMC via requirements in procure-ment contracts, developed in coordination with the Principal Cyber Advisor and the Chief Information Officer of the Department of Defense. The plan shall include a timeline for pilot activities, a description of the planned relationship between Department of Defense and the auditing or accrediting bodies, a funding and activity profile for the Defense Industrial Base Cybersecurity Assessment Center, and a description of efforts to ensure that the service acquisition executives and service program managers are equipped to implement the CMMC requirements and facilitate contractors’ meeting relevant requirements.
img credit: Etherwan (2018). NDAA Compliance Statement. Retrieved from: www.etherwan.com/us/about-…
-
You are Doing Cyberscecurity Awareness and Training Wrong

Let me tell you how most of my pitch calls go when someone needs instructional design work for their company’s cybersecurity awareness and training.
The customer typically says something along the lines of, “We just need a quick and dirty training, to check off the compliance box”.
I ask, “Can you send me your policies and procedures so I can weave them into the training?”
Response A:
“My boss doesn’t want this eating up a bunch of time and resources. We just need the compliance. This isn’t about learning.”
In the case of Response A, I always say, “Doesn’t it make sense to train your employees on your security stack based on their roles? Don’t you know policy and procedures mean nothing without people? We can write your awareness and training so it reflects your people, processes, and technology, and most importantly the threats the data you hold faces.”
Response B:
“We really don’t have the policies and procedures in place.”
For Response B, I always say, “Then your awareness and training needs to start with how to write and deploy policies and procedures.”
The Call Back
Almost always I get a call back an hour or day later with, “I talked to the boss. They want to keep it dead simple and focus on compliance. How much for a quick one hour training?”
I wish them luck and shut down the call.
-
Maturity models come to event logging for fe agencies www.whitehouse.gov/wp-conten… Per OMB’s response to Executive Order 14028
-
It came out of the kiln. Check it folks.
A-10 Warthog.
A limited signed and numbered 13 run as part of my efforts to support local artists through CMMC



-
Checked in to SENEDIA Defense Innovation Days

-
Checking out lasers and CUI enclave policies
-
hello
-
The Basics of Controlled Unclassified Information

When you cut through the marketing hype—and ignore all of the LinkedIn trolls predicting the doom of the Cybersecurity Maturity Model Certification (CMMC) program— you realize CMMC did not arise out of the blue. When you reasearch its history, you will find nothing especially new or unfamiliar. CMMC simply requires third party attestation of what defense contractors already had to do in order to fulfill the legal requirements of their agreements. The major change associated with CMMC is that it no longer allows for the self-assessment of cyber hygiene associated with Controlled Unclassified Information (CUI), as measured against NIST-SP-800-171 “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.”
Individual contractors no longer have the authority to say how well they secure CUI. Instead, a third pary must come in and assess this information. In essence, it all comes down to CUI. But what do we mean we say Controlled Unclassified Information (CUI)?
What is CUI?
The US Government defines CUI as information which requires safeguarding or dissemination controls necessitated by law, regulation, or Government-Wide Policy; however, it does not include classified or nuclear stuff. The latter two fall under classified policies, and therefore require even more protections than CUI.
The CUI program is thoroughly explained in the Code of Federal Regulation 32, Part 2002. This program standardizes how the Executive Branch handles CUI. The Department of Defense (DoD), for example, established a CUI policy on March 6th 2002. This policy, DoD Instruction 5200.48, “Controlled Unclassified Information,” fulfills their requirements to develop a CUI policy. Every department, and thus their respective agencies, must have a similar CUI policy.
The CUI designation was created in response to 9/11 via President Obama’s Executive Order 13556. This executive order required all unclassified information throughout the Executive Branch which necessitated additional protection above and beyond information not for public release to be labeled CUI. Before this CUI policy, no uniform marking system existed for this kind of information across the Federal Government. Different agencies used an alphabet soup of labels such as FOUO, LES, and SBU.
Under the Executive Order, the National Archives and Record Administration (NARA) was appointed to lead on developing a universal CUI Policy. The Secretary of Commerce, through the Office of Management and Budget, decided that CUI required moderate protection. FISMA, the Federal Information Modernization Security Act, then authorized the National Institute of Standards and Technologies (NIST) to develop standards for the protection of CUI.
In fact, section two of the Executive Order designated NARA as the Executive Agency to oversee the order and the CUI program. NARA delegated this authority to the Information Security Oversight Office (ISOO). ISOO established a CUI registry that is:
- Publicly Accessible
- Includes authorized categories
- Includes subcategories and guidance
- Includes citations to laws and regulation and government wide policies
The Department of Defense then defined their relevant categories using DoD Instruction 5200.48, “Controlled Unclassified Information”.
The ISOO CUI policy defines two types of CUI: Basic and Specified. Specified CUI contains specific handling controls, which it requires or permits agencies to use, and which differ from those used for Basic CUI. So, if a federal law or regulation requires handling instructions beyond the basic protections of CUI, we call this CUI Specified. An agency can decide internally, or with agreement from ISOO, to require additional protections.
CUI Lifecycle
The CUI lifecycle requires a contractor to identify the CUI they handle, to explicitly mark this data as CUI, to protect this CUI while in transit and at rest, to only share CUI for a lawful purpose, to destroy CUI when necessary, and to decontrol CUI when it no longer needs additional security.
Identifying CUI
It is best to begin this process by determining if you have any CUI in your system, or if you wish to bid on future contracts that would require CUI in your systems. Unfortunately, most of the data contractors receive from the DoD and prime contractors will not have proper markings. This does no alleviate a contractor of the legal responsibilities for protecting CUI, especially if they have existing contracts with the Defense Federal Acquisition Regulation Supplemental (DFARS) clause 7012, which requires self-attestation for protecting CUI against a 171 baseline.
Once you identify the CUI in your system, identify which contract vehicles with a 7012 clause the CUI is often associated with. Then identify the people or roles with legal access to that CUI under each contract. In fact, you should create a matrix to capture this information.
You cannot expect the DoD or a prime contractor to label all CUI created under a CUI contract. How could a Contracting Officer (CO) or a Program Management Office decide if the personal notes taken or meeting minutes contain CUI?
Marking CUI
The CUI program set out to protect unclassified information and ensure the timely sharing of information. The marking requirements of CUI vary based on the kinds of CUI and the chosen designation indicator. These influence the requirements for banner markings, which have to include category markings, control markings, and any limited dissemination markings (only certain people should see this).
CUI marking requirements are influenced by more than just their category and control markings. The type of media it is associated with, such as emails or military documents, can influence the marking as well. Email banners may differ from the requirements for removable media. CUI can also be co-mingled into documents that require different limited dissemination, or are considered classified. Finally, you also have rules about marking CUI for mailing.
The marking must include a designation indicator. This indicates who created the CUI. This can include a variety of formats such as a letterhead, a logo on a sticker, a signature, or a controlled byline. You have no requirement to include contact information, but many markings add this optional information.
Department of Defense guidance suggests using a Designation Indicator block when space allows. This includes who controls the data, as well as anyone to which control was flowed through an authorized and legal use, any limited dissemination controls, and a point of contact. For example:
Controlled by: OUSD(I&S)
Controlled by: CL&S INFOSECCUI Category(ies): PRVCY, OPSEC
Limited Dissemination Control: FEDCON
POC: John Brown, 703-555-0123
The banner marking can include three elements. The first, the control marking, is mandatory. This can say “controlled” or “CUI.” Category markings are required for CUI Specified, and are separated by two // slashes. If dissemination controls are included, those follow the category markings, again after two forward slashes. Banners must appear in Bold Capitalized text, and ought to be centered when possible.
CUI works as a basic CUI label.
Category markings are optional, except in the case of CUI Specified. In fact, when you have Specified CUI, you are required to include the letters SP before the category marking. If more then one type of specified marking is included, you alphabetize them, but only separate each by one / forward slash after the first category, which follows the two // forward slashes and the basic marking.
CUI//SP-HLTH/PHYS In this example we see two CUI specified categories which follow the basic CUI marking.
The banner markings can also designate the dissemination controls. Limited Dissemination Controls identify an intended audience, so a document does not need continuous authorization.
No Foreign Dissemination (NOFORN) —Information may not be disseminated in any form to foreign governments, foreign nationals, foreign or international organizations, or non-U.S. citizens.
Federal Employees Only (FED ONLY) —Dissemination authorized only to employees of the U.S. Government executive branch agencies, or armed forces personnel of the U.S. or Active Guard and Reserve.
Federal Employees and Contractors Only (FEDCON) —Includes individuals or employees who enter a contract with the U.S. to perform a specific job or supply labor, and dissemination is in furtherance of the contractual purpose.
No Dissemination to Contractors (NOCON) —Intended for use when dissemination is not permitted to federal contractors, but permits dissemination to state, local, or tribal employees.
Dissemination List Controlled DL ONLY —Dissemination authorized only to those individuals, organizations, or entities included on an accompanying dissemination list.
Authorized for Release to Certain Foreign Nationals Only (REL TO USA, LIST) —Information has been predetermined by the designating agency to be releasable only to the foreign country(ies) or international organization(s) indicated, through established foreign disclosure procedures and channels.
The Department of Defense CUI guidance also allows dissemination marking to be included in the designation box. These include:
Distribution Statement A: Approved for public release. Distribution is unlimited.
Distribution Statement B: Distribution authorized to U.S. Government agencies only (fill in reason and date of determination).
Distribution Statement C: Distribution authorized to U.S. Government agencies and their contractors (fill in reason and date of determination). Other requests for this document shall be referred to (insert controlling DoD office).
Distribution Statement D: Distribution authorized to Department of Defense and U.S. DoD contractors only (insert reason and date of determination). Other requests for this document shall be referred to (insert controlling DoD office).
Distribution Statement E: Distribution authorized to DoD Components only (fill in reason and date of determination). Other requests shall be referred to (insert controlling DoD office).
Distribution Statement F: Further dissemination only as directed by (insert controlling DoD Office and date of determination) or higher DoD authority.
On digital media, you include these markings. On PowerPoint slides, you can include the CUI label at the top and bottom of the title slide with the indication block and the CUI label on the bottom of each slide. In a word document, you can include a cover sheet with the marking and designation block.
Removable Media
On a removable storage device, you are required to include the basic marking and a controlling indicators. Each file contained on the storage device needs its own marking. When feasible, you should include all required elements in the designation block, but the CUI basic marking and the originator or controller must always be included.
Email
Email is a bit trickier. When you send an email (try not to) containing CUI, you must let the recipient know. You must include a banner marking in the body of the email. Furthemore, best practice suggests including it in the CUI itself. Many companies use email server rules to sequester email with CUI. The subject line helps protect the data. When you forward email you must keep all banner markings. Make sure you cut and paste the banner to the top of the forward. You can also portion mark emails like regular documents where you call out sections that contain CUI.
Physical Protection of CUI
You will need to create a controlled environment to protect CUI. The regulations require you to have at least one physical barrier, such as sealed envelopes, locked doors, bins, drawers, or electronic locks. You have flexibility in deciding what counts as a physical barrier.
You also need to consider meeting areas. You will need to control meeting access when CUI is shared and discussed. You will need to mark the door with the lock, noting only authorized indivduals allowed, and you will need a clean desk policy for after the meeting.
Think about who has access to your controlled environments. You will need to lock away CUI from after hour cleaning crews, and to keep visitor and employee logs of areas that contain or discuss CUI. Your computer systems and networks also need to control access. You need to include banner markings on devices and systems that can connect to controlled environments.
Basically, on electronic systems, you need to create some kind of barrier to prevent unauthorized access to CUI. This can include network folders, files, intranet, cloud enclaves, file sharing sites, and individual machines or devices.
Encryption and CUI
Based on Office of Management and Budget (OMB) policy, CUI requires moderate protection. This, in turn, requires encryption which meets a specific level called FIPS Validated 140-2A. At the simplest definition, encryption means that something we read in plain text is scrambled into a cyphertext. The authorized holder then has a “key” to unscramble the ciphertext into plain text.
The approved encryption techniques are authorized by NIST in a document called “Federal Information Processing Standards (FIPS) 140-2.” The approved techniques, which can change based on use case and authorizer, include: AES, Triple-DES, and the Digital Signature Standard (“DSS”). NIST-SP-800-171 (3.1.13 and 3.13.11) and CMMC spell out specific requirements for encryption (AC.3.014, SC.3.177).
With FIPs level encryption, we make an important distinction between modules and devices. A module can be an embedded part of a product, such as an “encrypt this email” button or an entire product such as a CUI cloud enclave. A device, such as a laptop or cellphone, does not itself need the encryption. The tool accessed on that device to share, view, store, or transmit CUI must use encryption modules that meet FIPS standards.
Destroying CUI
When you destroy CUI, the NARA policy CFR 32 Part 2002 requires the CUI to end up unreadable, indecipherable, and irreconcilable. The NARA policy follows guidance of National Institute of Standards and Technology (NIST) Special Publication (SP) 800-88, Revision l: “Guidelines for Media Sanitization” or any technique approved by Classified National Security Information (32 CFR 2001.47).
In 2019, NARA released guidance on destroying paper-based CUI. You must follow the specifics of NIST-SP-800-88 when shredding paper. You must crosscut, meaning up and down, and left and right, down to 1mm x 5mm (0.04in x 0.2in) in size. You can also pulverize paper using disintegrator devices equipped with a 3/32in pulverizer. The approved shredders can get expensive. Many companies use a third party shredder or recycler that will provide a certification that they meet the requirements of NIST-SP-800-88.
You can always go the cheapest route and follow the burn recommendations.
In terms of media, there are also destruction requirements. NIST SP 800-171 3.8.3 states, “Sanitize or destroy system media containing CUI before disposal or release for reuse.” The type of media will determine how you sanitize the device. Hard drives, for example, need different disposal methods than static hard drives.
Decontrolling CUI
CFR 32 Part 2002 defines decontrolling as the event in which the authorizing agency decides the CUI “no longer requires such controls.” You must have policies and procedure in place to decontrol CUI. CUI can be decontrolled automatically or through positive decontrol. In automotive decontrol, a prior event, such as a date, is chosen when the controls are no longer required by law or policy. In positive decontrol, the authorizing agency takes an action to remove the controls.
While a contractor can be appointed by the authorizing agency to disagree with the ability to decontrol CUI on a contract with the 7012 clause, it will not happen often.
In the end, when you think CMMC, just think about CUI and how you can protect it from unauthorized disclosure.
-
Looking for a good Risk Awareness training program? Why not start with NIST-SP-800-30?
-
Another great meeting of the CT CMMC Coalition
-
A must read —The Coast Guard 2021 Cybersecurity outlook www.uscg.mil/Portals/0…
-
CMMC and Ethics

At a recent Town Hall, the Cybersecurity Maturity Model Certification Accreditation Board (CMMC-AB) CEO Matt Travis noted that “trust and confidence in the CMMC Ecosystem” is the shared responsibility of both the AB and the members of the community.
In fact, Travis’s call to action harkened back to the the testimony of Deputy Assistant Secretary of Defense for Industrial Policy Jesse Salazar, who noted in his testimony to the Armed Service Committee cybersecurity subcommittee:
DoD must ensure there are clearly defined roles and responsibilities, standards of conduct, and audit mechanisms governing relationships with private sector entities within the external assessment system.
In order for CMMC to succeed, ethics must matter.
In the realm of Cybersecurity Maturity Model Certification, the Professional Code of Conduct drives ethical considerations. This document provides the standards to which all members hold themselves accountable.
The document unites around five principles:
- Professionalism
- Objectivity
- Confidentiality
- Proper Use of Methods
- Information Integrity
The document then lays out the practices inherent to each principle, in addition to how reporting features are implemented.
Conflict of Interests occur when a person has a duty or motivation to serve the interests of more than one party in the engagement of an activity. According to Matt Travis, this can lead to a variety of consequences, including:
- Compromised Judgement
- Threatened Objective Decisions
- Undermined Impartiality
- Destroyed Confidence in Fairness and Integrity
- Required Disclosure
CMMC Conflict of Interest
We must remember that a mere perception of conflict can cause serious damage, even when no such conflict exists. Conflicts of interest can also exist without malicious intent or outcomes.
The CMMC-AB, in fact, must establish a firewall between the registration of consultants, the accreditation of training schools, and the Assessment of Organizations Seeking Certification (OSC).
Section 3.1.8 of the CMMC Professional Code of Conduct (CPCOC) requires everyone to avoid conflicts of interest to the greatest extent possible. We have a duty to avoid conflicts and report them when they occur.
The professional code of conduct in Section 3.1.10 also prohibits Certified Third Party Assesment Organizations (C3PAOs) from soliciting business from the organizations they assess. In other words, you can not fail an OSC and then offer services to help them pass the next assessment.
CMMC and Objectivity
The CPCOC prohibits a credentialed assessor from joining an assessment team if that individual helped the organization prepare for the assessment.
The ecosystems of many companies have Registered Professional Organization (RPO) credentials and C3PAO credentials. A business can not provide RPO services and then join a C3PAO Assessment Team, or host an Assessment Team themselves. Furthermore, if you have signed the CPCOC, you have an obligation to report this activity if you see it.
CMMC-AB and Ethics
In order to understand how the Accreditation Board (AB) must adhere to the ethics of the CPCOC, we must first understand their role in the ecosystem. The AB is required to:
- Authorize CMMC C3PAOs to conduct assessments
- Accredit C3PAOs in accordance with ISO 17020
- Authorize the CAICO (CMMC Assessors and Instructors Certification Organization) to certify CMMC Instructors and Assessors
- Establish, maintain, and Manage the CMMC Marketplace
- Oversee the CMMC Professional Code of Conduct
Due to these roles the CMMC-AB has a variety of tools to limit Conflict of Interest
- CMMC-AB Code of Ethics
- CMMC-AB Conflict of Interest Policy
- CMMC-AB Directors Agreement
- CMMC Code of Professional Conduct
- Contract with Department of Defense
- CMMC-AB Audit, Ethics, and Compliance Committee
- Security and Compliance Officer
- ISO 170ii General Requirements for Accreditation Bodies Assessing and Accrediting Conformity Assessment Bodies
These elements work together to ensure the CMMC ecosystem maintains a high ethical standard.
Duty to Disclose
The CMMC-AB will release a disclosure matrix that lists all of the players in the ecosystem, and then a list of possible affiliations. These include elements of potential conflict such as ownership, financial interest, teaming agreements, family members, personal relationships, employment affiliations, and more. The AB will decide if, based on its role in the ecosystem, if that is a type of relationship that is okay, to be avoided, or risky enought to require mitigation.
This document will explain your responsibilities to report conflict of interest.
Red Lines for the CMMC-AB
Based on the policies governing the AB, its members must not fail to disclose conflicts, have a vested interest in an C3PAO, use their status on the AB to generate business or leads, endorse any commercial product implicitly or explicitly, accept any gifts, or operate in a credentialed company within the ecosystem for the duration of one year after leaving the board.
Shady Vendors
As a member of the ecosystem, you face a barrage of emails. Many of these provide snake oil services or over-promise. As a small business, owners rely on word of mouth, not drip campaigns from marketing teams. Avoid anyone who promises quick assessments or turn key services.
Take your time. You do not need a Level Three Certification overnight. 2026 is still a bit far off. Until then, just grow the SSP and shrink the POA&M.
-
CyberSecurity Begins with Awareness and Training

It always comes down to the humans. Even with the best security, the tiniest friction can cause all systems fail. That 2% of DNA separating us from chimpanzees really messes with your cyber hygiene.
If you want security you need to focus on the biggest attack vector: people.
The Cybersecurity Maturity Model Certification (CMMC) program revolves around a national awareness and training program to increase the validity and reliability of the cybersecurity hygiene for the Defense Industrial Base (DIB).
Relying on self-assessments hurts the overall validity of an organization’s cyber hygiene, due to the scoring system for determining compliance. In NIST-SP-800-171 nor 171a, the methodology describes a scoring scheme. That model of having 110 points, and subtracting either 1, 3, or five points, came from the Defense Contracting Management Agency (DCMA). It did not work.
Relying on self-assessments hurt the overall reliability of knowing if someone had achieved adequate compliance against NIST-SP-800-171. A lot of revenue depends on contracts from the Department of Defense that carry the 7012 clause. Many companies lacked experience or have had past success with a business development strategy of ignoring Department Defense mandates .
We use the amount of data exfiltration from small manufacturers as proof of the failure. The daily ransomware attacks DIB companies face is further observable evidence that self-assessment does not work.
CMMC requires us to realize cybersecurity isn’t just everyone’s job. Cybersecurity IS everyone. You must control your story, data, and identity. The people matter.
In fact, the CMMC model requires an Awareness and Training Policy for Level Two (and thus Level Three, given the cumulative nature of the model):
AT.2.999
Establish a policy that includes Awareness and Training.
So how do you build an Awareness and Training policy? You need to understand what people need to know, when they need to know it, and how you will prove they know it. This begins, like all learning, by definining key terms.
What is Awareness?
I can understand the dangers of swimming in riptides in the absence of the training to escape one. All employees must have an awareness of the threats your company faces.
In fact NIST SP 500-172, defines awareness as
sensitivity to the threats and vulnerabilities of computer systems and the recognition of the need to protect data, information, and the means of processing them
However, awareness—like swimming—does not equal training. In terms of cybersecurity, a company needs to have a general understanding of threats and cyber hygiene in order for it to grow. So, for example, while I may hang Controlled Unclassified Information (CUI) posters in the enclave to keep people aware of company policies, that does not equal a training program on selecting the correct shredder for the destruction of paper-based CUI.
You may publish many of your policies in an employee handbook to make them aware of security issues. But you still need to train employees on how to execute these policies.
What is Training?
Awareness focuses on what, while training focuses on why and how. Training will take longer, and you as the learner will need to generate observable evidence of knowledge growth.
What Type of Awareness Programs do my Employees Need?
Based on the NIST 800-171a assessment objectives included in CMMC, you have to have an overall awareness of the threats CUI faces. All employees need an awareness of policies, standards, and procedures. This is often best covered in the Employee Handbook and Acceptable Use Policies.
Your technical staff will need to understand the security risks associated with their activities to keep data safe. This, again, will require the development of Operating System awareness, and you may need to run multiple awareness programs for each major and minor technical system.
Managers and system administrators need awareness of the applicable policies, standards, and procedures related to the security of the systems they oversee. This will include reference documents, a required tour of a wiki or database, and Security Technical Implementation Guides (STIGs).
Some Awareness and Training requirements kick in at Level Two when we talk Cybersecurity Maturity Model Certification (CMMC):
AT.2.056
Ensure that managers, systems administrators, and users of organizational systems are made aware of the security risks associated with their activities, and of the applicable policies, standards, and procedures related to the security of those systems.
ASSESSMENT OBJECTIVES [NIST SP 800-171A]
Determine if:
- [a] security risks associated with organizational activities involving CUI are identified;
- [b] policies, standards, and procedures related to the security of the system are identified;
- [c] managers, systems administrators, and users of the system are made aware of the security risks associated with their activities; and
- [d] managers, systems administrators, and users of the system are made aware of the applicable policies, standards, and procedures related to the security of the system.
To meet the assessment objectives of this practice you will need to provide multiple types of security awareness and training programs
What type of Training Program Do My Employees Need
Based on the NIST 800-171a assessment objectives included in CMMC, you have to have three domains of training. One domain is focused on your CUI policy, another on threat analysis, and another on your system, security, and roles.
CMMC has an entire set of objectives on developing and deploying a CUI policy. In your training, you need to ensure your managers and technical systems engineers, or Managed Service Providers (MSPs), know how CUI is protected on your system.
Your training around applicable policies, standards, and procedures related to the security of the system will need extensive documentation, and will include recognizing educational certificates and providing your own training related to your reference architecture.
For example, take AT.2.057, which requires contractors to “ensure that personnel are trained to carry out their assigned information security-related duties and responsibilities. ” This will require operating system training specific to a company’s reference architecture. You will rely on different certificate programs to ensure your technical staff can stay current as technology changes. You will need multiple trainings for each of the operating systems deployed on your major and minor systems that store, transmit, destroy, or create CUI as the result of a government contract.
What is the Purpose of my Awareness and Training Policy?
The first objective of AT.2.999 establishes a policy that includes Awareness and Training, which requires you to have a purpose to your awareness and training policy. For Level Three certification, you need a mission and strategic goals. AT.3.997 requires contractors to “establish, maintain, and resource a plan that includes Awareness and Training” objectives b and c.
We recommend you do this on company-wide scale, via a threat awareness and training program. Explore the threats, external and internal, you face. Analyze risks to your business and supply chain.
Break employees into groups and have them draft threat analysis documents (this is a Level Four requirement, but wise to implement ahead of time). Then when you have a complete list of threats, have the groups craft mission and goal statements.
You then work with the groups in a whole company setting to ensure your employees draft the kind of comprehensive policy statement you envision. Ownership builds awareness.
Many mature and large organizations will have awareness and training policies developed. If this is the case for your organization, you should still conduct ongoing threat analysis discussions at the department level.
At the end of the day, make sure folks are aware.
Who needs Awareness and Training?
Everyone. Awareness and training ensure policies and procedures become company culture. However, it is important to note that your managers, sales staff, and security engineers need different awareness and training.
NIST Special Publication 800-16, “Information Technology Security Training Requirements,” recommends creating a role-based training matrix. You can combine this approach with CMMC requirements to create a full curriculum scope and sequence for your awareness and training program.
In the first column of the Matrix, list all the user roles on your information systems. Include a row for “all.” You can group trainees by their roles as well.
Then create four domains in your awareness and training program:
- Employee Responsibilities,
- Information System Policies,
- CUI
- Reference Architecture
What kind of training an employee receives, and in which domain, depends on their role. For example, all employees may have to watch a training and certify they read the Employee Handbook and Acceptable Use Policies. You probably want a training on the email rules of your company for all employees.
For Level Three CMMC Certification, you need to document what will be learned. In fact, Assessment Objective [e] of AT.3.997 requires you to document “the plan documents, activities, and due dates.” In your matrices, be sure to list the trainings, in addition to when due dates occur.
Fill out the chart indicating when role-based awareness and training occurs, what it includes, and how it is assessed.
Large companies may have an internal learning management system that may track many of these metrics. Smaller companies may have to contract with a vendor. If you purchase IT or security products from MSPs or vendors, try to negotiate a training package, or choose those you see as compliance partners.
What should Awareness and Training Cover?
Employee Responsibilities
You need to cover the four domains of knowledge, but now you must also develop the scope of learning objectives and the sequence of training for the matrices.
First begin with employee responsibilities by examining the everyday system-wide awareness and trainings all employees must receive. This includes the employee handbook, sexual harassment, legal compliance, company wide posters, CUI handling posters, and stickers. These are everyday business practices that require awareness and training.
Then decide which of these policies need more than awareness and actual training. This could include a short video summarizing the employee handbook with a quiz. Employees often have to attend mandatory trainings with a supervisor.
Once you have the list, decide if the subject requires awareness or training. Add it to the matrix.
Controlled Unclassified Information
As noted above, you must include awareness and training on the “security risks associated with organizational activities involving CUI are identified.” In other words, you need to develop a CUI Training Program.
At Level Two of the CMMC, your company will need awareness and training on the internal threats faced by companies who have a legal right to handle Control Unclassified Information on behalf of a government contract.
At Levels Two and Three, your awareness and training program must include your company policies on receiving, creating, labeling, disseminating, transmitting, storing, and destroying CUI. This policy should cover the specific workflows for handling this information. You will also need to include your Incident Response Training on handing CUI data spillage.
At Level Four, your CUI awareness and training program should include recognizing and responding to threats from social engineering that can lead to advanced persistent threat actors, breaches, and suspicious behaviors; you will be required to update the training at least annually, as well as when there are significant changes to relevant threats.
Information System Policies
Then you will have company-wide information system policies, such as your password policy, email policy, device policy, how Multifactor Authentification works (please turn on MFA), et cetera.
These Information System Policies apply to all employees, however, at this point you may have to start specializing. The account generation for your Mobile Device Management tools may vary from your payroll system. In fact, at this level you will start to specialize at the Operating System level.
Different types of operating systems will require you to verify employee training through different certificates. If you deploy in Kubernetes in Azure or use S3 in WS Govcloud, each of those stacks has individual Security Technical Implementation Guides (STIGs) and certification programs.
You must consider all the major and minor systems, the data that flows through them, and the laws and regulations that govern how that data is used and shared.
As a contractor, you also will need to consider trainings on your acquisition team on what kind of service level agreements you need in your vendor agreements with regards to information and technology systems. Trainings need to include examining vendor agreements and SLAs to determine if proposed security solutions meet CMMC Level Three standards.
Reference Architecture
As Tom Cornelius from Compliance Forge notes, “You must see policy as a blueprint and not documentation. You are more an archtiect than a writer.”
As an organization, you will need solid reference architecture on how you build secure systems that can handle a moderate baseline for the protection of Controlled Unclassified Information. You will have a set of documents that describe how to build the ideal environment for your use case. You will need awareness and training on how to use and update your reference architecture.
Take configuration management for example. If you do not have a clear configuration management documentation and provide baseline training on using the necessary references, you will not have the basics of Access Control, the root of cybersecurity.
Next, you can turn to the other domains in CMMC to determine the specifics of company-wide training policies.
What other Domains Should Awareness and Training Cover?
The Awareness and Training you provide must go well beyond the practices and process of the AT domain. In fact, according to Native Intelligence in a blog post on Amira Armond’s CMMC Audit, Awareness and Training needs to cover fourteen additional practices across five domains
- Access Control (AC)
- Media Protection (MP)
- Maintenance (MA)
- Physical Protection (PE)
- Systems and Communications Protection (SC)
How to Get Started on an Awareness and Training Plan
Create an Instructional Leadership Team
You first begin by designating who owns your awareness and training program. The Instructional Leadership Team should contain stakeholders across the organization and not just from IT or your security team (if you even have either position. The team could include your Information System Security Officer, CIO, CTO, information System Security Manager, human resources, facility security officer, or employees designated to serve on the instructional leadership team.)
Craft Goals, Missions, and Objectives
Your instructional Leadership Team then crafts your goals mission and objectives. This begins by a walkthrough through of your threat environment. Understand the common threats to the sensitive data you hold.
You can have very generic goals, missions, and objectives for your trainings. You may want to consider utilizing the awareness and training domain to strengthen your talent across the board. However, you only need to track system security related training with CMMC.
Determine Roles for Awareness and Training
Next, the Instructional Leadership Team determines roles and responsibilities. Christina Reynolds of BDO-USA recommends using the RAC model: who is Responsible, who is Accountable, and who need to be Consulted. The goal is to create observable evidence that partially meets assessment objectives c, d, and g of AT.2.999
” the roles and responsibilities of the activities covered by this policy are defined; (i.e., the responsibility, authority, and ownership of Awareness and Training activities);”
“The policy establishes or directs the establishment of procedures to carry out and meet the intent of the policy;”
“the policy is endorsed by management and disseminated to appropriate stakeholders; and “
So you develop a matrix of roles and responsibilities. Include general users, data owners, system owners, and members of the Instructional Leadership Team. Make a column for each.
Then, in the rows include who must complete training, who develops the training program, who agrees to acceptable use policies, who decides which roles get what training, who completes role based training, and who is responsible for record keeping.
Establish Company-wide Baselines
Now, decide what basic training every employee must have. This will include your awareness activities, employee handbooks, email policies, acceptable use policies, etc. You may include optional training on overall threat awareness and common attack vectors, such as phishing.
The goal is to establish the bare minimum of security awareness you want with your employees. This wil usually include a variety of trainings like company wide meetings, video on-demands, or online learning.
Develop A Training Matrix
Now that you have a baseline of security awareness and training you want for employees, you next decide on specialized roles, and create a role-based training matrix. People in specialized roles and management positions will need additional training over and beyond what every employee recieves.
You need to group people into roles based on functions in the workplace.
Then create a list of topics, which includes items such as:
- CUI
- Threat Awareness
- Media Protection
- Passwords
- Mobile Devices
- Access Control Policy
- Reference Architecture
- Crafting Service Level Agreements
- etc
You then decide based on the number of roles created by your Instructional Leadership Team which group gets what training.
Develop Company Wide Awareness and Training Rubric
Next the Instructional Leadership Team needs to define success metrics for your awareness and training program. In terms of CMMC, it is important to know if a plan really does not kick in until Level Four process requirements, but you cannot have a compliant training program at this Level without evidence of learning gains.
The evidence of awareness and training success, like all compliance data, can fall into one of three categories: interview, observe and test.
First, you want to understand if your awareness and trainign impacts your operational security. Indicators could include reduction in down time, increased phishing test success rates, and incident reporting. If you can not automate these metrics, you can have the Instructional Leadership Team rate them on a four point likert scale.
You also have training program metrics, such as the frequency of training programs, learner performance, attendance, and learner feedback. You should check with your state on the requirements to protect and retain employee training data.
Evaluate Content
Now you have to choose content that will align your role based matrices with your required learning matrices. It will probably be cheaper to purchase curriculum than to develop it in-house. However, when you pay for an instructional designer to develop your program, you can align the program to your company culture and workflow.
The majority of cybersecurity training is video-based garbage designed to allow you to check off a compliance box about providing training. Develop or utilize a rubric for evaluating curriculum. You may consider hiring a consultant to help you evalaute curriculum. At the very least, choose your networks from word of mouth.
Create Deployment and Evaluation Schedule
Next, you must create a scope and sequence guide for your curriuclum. This document includes the objectives of your chosen curriculum, how those objectives will be measured, when the curriculum will be delivered, and who will evaluate the result. You can include information about awareness and training.
For awareness, you could include the posters you hang and monthly security reminders that are delivered by email. The awareness program occurs all the time, and for all users.
For training, this again will be a role-based document. Many people may end up including the role-based matrix in the scope and sequence of the curriculum.
Craft Awareness and Training Plan Compliance Documentation
Finally, you will need to create a way to document your awareness and training program, so you organize observable evidence in a way that would not require a CMMC assors to make any inferences about your program. Spell out how you meet each requirement in your Policy, Procedures and Plans. If you followed the path above, you will have the majority of the required documentation already.
Now, as your goal you must include the procedures you have decided upon for your Awareness and Training Policy, in addition to how you plan to include the metrics from your Awareness and Training in both your System Security Plan (SSP) and your Awareness and Training Plan.
Create a policy for retaining security training records. Create the procedures to make sure this happens.
Include a table in your policy that explicitly addresses all of the required Awareness and Rraining in a practice or assessment objective. Then, in your SSP, reference this policy and include two pieces of observable evidence that the assessment objectives have been met.
For example, you need to include training of internal threats at Level Two of CMMC. This means that for Level Three compliance, you must demonstrate you provide this training. Explicitly spell this out, in addition to any required training in your Awareness and training Policy and Procedures.
For many companies, beginning with the Awaress and Training domain may provide a great launching point for your CMMC journey.
Meet CMMC Compliance through Awareness and Training
Can you complete your SSP as you utilize and also reach compliance on the Awareness and Training domain? Would this approach lead to increased hygiene?
Everyone frets over CMMC devolving into a checklist of policy and confusing technical controls. Awareness and Training makes this difference.
Christina Reynolds co-authored this post in the guidance she provided in how to craft Awareness and Training Policy
Featured Image: “Bad Ragaz - Original Sin” by Kecko is licensed under CC BY
-
Roots of CyberSecurity
So many people complain bout the forest and trees in the world of cybersecurity. Some look to the trees and can write 5,000 word essays pulling about the etymology of a single word. They never see the forest.
“Forest Turnover” by Nicholas_T is licensed under CC BY
Others claim cybersecurity frameworks such as the Department of Defense’s Cybersecurity Maturity Model Certification will rise only to find itelf destined to fail. These critics note a piling up of assumptions and technical debt. They point to the Forest of compliance efforts like ISO or unjustly complain SOC2 compliance comes from gumball machines. They never take the time to see the trees.
Yet we need to stop worrying about the forest and trees of CMMC. Cybersecurity happens underground, through your culture. You must grow cyber hygiene in rich soil. Do not look to the forest or the trees. Instead get to the roots of cybersecurity and the fungus that keeps it alive.
Roots of Cybersecurity
The root system of any tree expands 20 times the size of the canopy. Often when we think trees have died around us, being returned to the earth by, you guessed it fungus, the trees go on living underground. Their roots living for years, decades, possibly centuries keeping other trees alive. Connected through a network of fungus.“DSC01648” by Clearly Ambiguous is licensed under CC BY
We must see cybersecurity as a symbiotic relationship between the public and the private sectors. You as a business owner need to understand that without some basics you can never secure sensitive data, and if you can’t secure sensitive data you will never get past the basics.
Around 90% of land plants thrive in mutually-beneficial relationships with fungi. Yet we do not see it. The mycelium, network of fine white filaments that make up the vegetative part of fung, exist out of sight. It just happens. We need this in cybersecurity.
“Mushroom, NCI Sourdough trail” by furtwangl is licensed under CC BY
Symbiotic relationships.
The plants and trees allow the fungus to siphon off food and the fungus help the plants eat, act as a network of advanced persistent threat, and fight of pests. In a cubic inch of soil you can find 8 miles of mycelium. We must get to a similar state of cybersecurity, hidden underground protecting our networks.
To deliver food plants provide fungi with carbohydrates. The fungi suck up water, and provide nutrients like phosphorus and nitrogen, via their mycelia.
The fungi also create a network to support each other. Paul Stamets, back in 1970 compared the mycelia of root systems to ARPANet, what we now call the Internet. Further According to Suzanne Simard older trees adjust the fungal network to help younger trees. They can redirect carbon they collect in their canopies to children of the forest floor who hide in the shadows. Protected by larger organisms.
“Rhizomic” by mikecogh is licensed under CC BY
The Wood Wide Web, also like cybersecurity provides advanced persistent threat analysis. When fungus in the roots recognize a threat they trigger the production of defense-related chemicals. These make later immune system responses quicker. When one tree gets attacked by harmful pests or deadly fungi, the mycelium can set off a chemical response in the root system to warn other trees.
We need to get to the roots of cybersecurity and this this includes five elements. You must do every one of these first.
Governance
First in terms of Governance who owns your data, who owns your systems, who maintains the System Security Plan? The mycelium under the trees acts as a microbial neural background. The management.
When you look at mycelium and a node breaks the network moves around it. You must have a plan to handle cybersecurity and know who will enforce policies.
Policy
Fungus migrated from the sea to land millions of years before plant life. The acids they produce broke down calcium in the rocks and produced soil. Your policy does the same thing.
The fungi worked by acting as carbon sinks. Fungus got the system working just as your policy is required for cybersecurity. In fact you should begin with writing a policy of how your company writes policy. You may in fact have a ton of existing policy but you can not protect what you don’t know you have.
Inventory
After the great extinction event that killed the dinosaurs the fungi inherited the earth. They could grow in the dark and even use radiation as food. The largest mycelium organism sprawls across 2,200 acres of Oregon and has lived before the time of the Christian Era. You need to know the spread of sensitive data, endpoints, and people.
Have you counted them all? If you do not have a solid inventory system you can not have security. You need to know how sensitive data spread through your network for without an inventory it will spread like a rhizome, like mcyelliumn
Access Control
Paul Stamets has long argued that the Internet just provides proof of concepts that already exist. The mapping of Internet traffic and Dark Matter all reflect the mapping of the rhizomatic spread of the rhizome.
You will need to keep a compliance machete at the ready to control access to sensitive data. Fungus act gateway species. Stamets note they let other life in. In fact he creates physical and logical barriers of mycelium downstream from farm to remove excess fertilizer and deadly diseases like e. Coli.
Awareness and Training
As he studies the fungus of the world Stametz tries to preserve the genome. In fact in collaboration with the Department of Defense they discovered five ancient and almost extinct fungi in the old growth forests that could help fight poxxed based diseases.
Ancient forests in China contain fungi that fight Flu and SARS.
Saving our old growth forest is a matter of national security. Just like your cyber security.
Let’s get to the root of the issue
-
Everyone should read this: FEDERAL CYBERSECURITY: AMERICA’S DATA STILL AT RISK
subscribe via RSS




