-
As always, better cybersecurity is better business
You need to be be aware
Good backups save all the bucks

-
Almost all cybersecurity frameworks and government regulations require small businesses to periodically test your backup recovery systems.
You need to make sure you can test processes and cloud solutions while training employees
You need to run practice exercises

Improve
-
Small business owners often overlook on area of risk that allows attackers a chance to get your data.
Your backup policy needs to spell out how long copies get kept and the proper way to destroy sensitive data
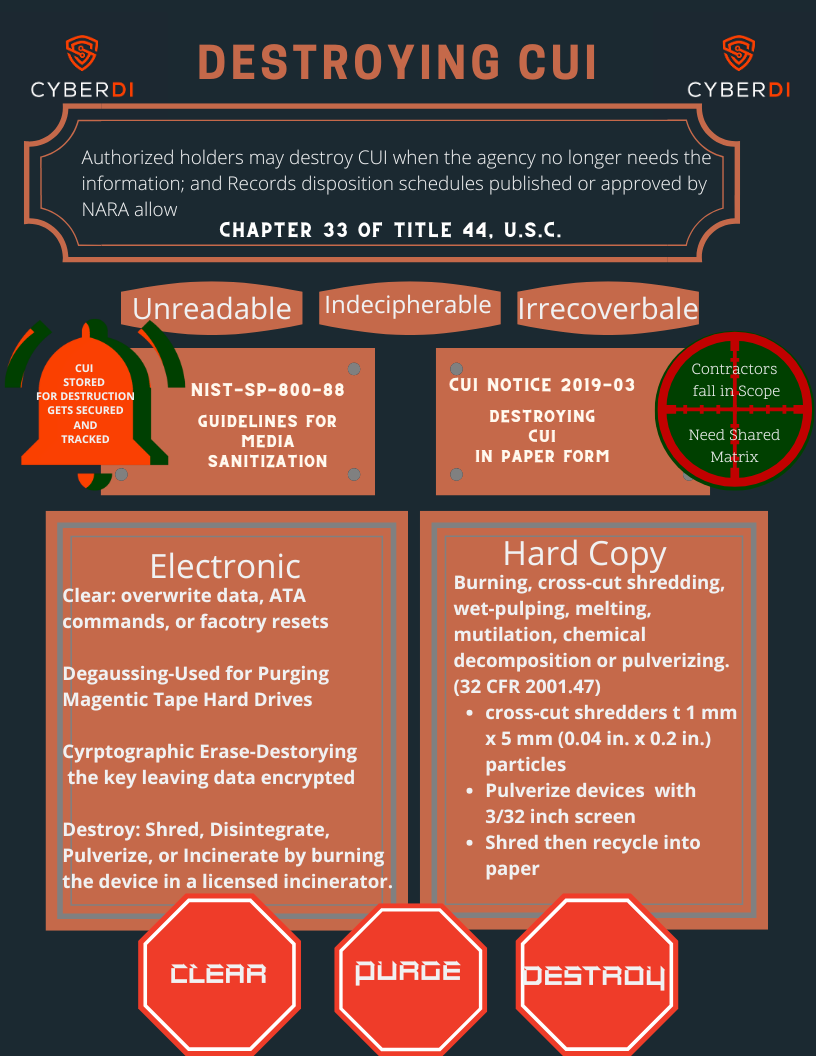
-
Once you have policy and procedures in place you should deploy the backup system
Means protecting backups
It is at this stage where most bad guys break into your stuff and screw it all up.
You need protect the backup system at all times and most involve shared responsibility
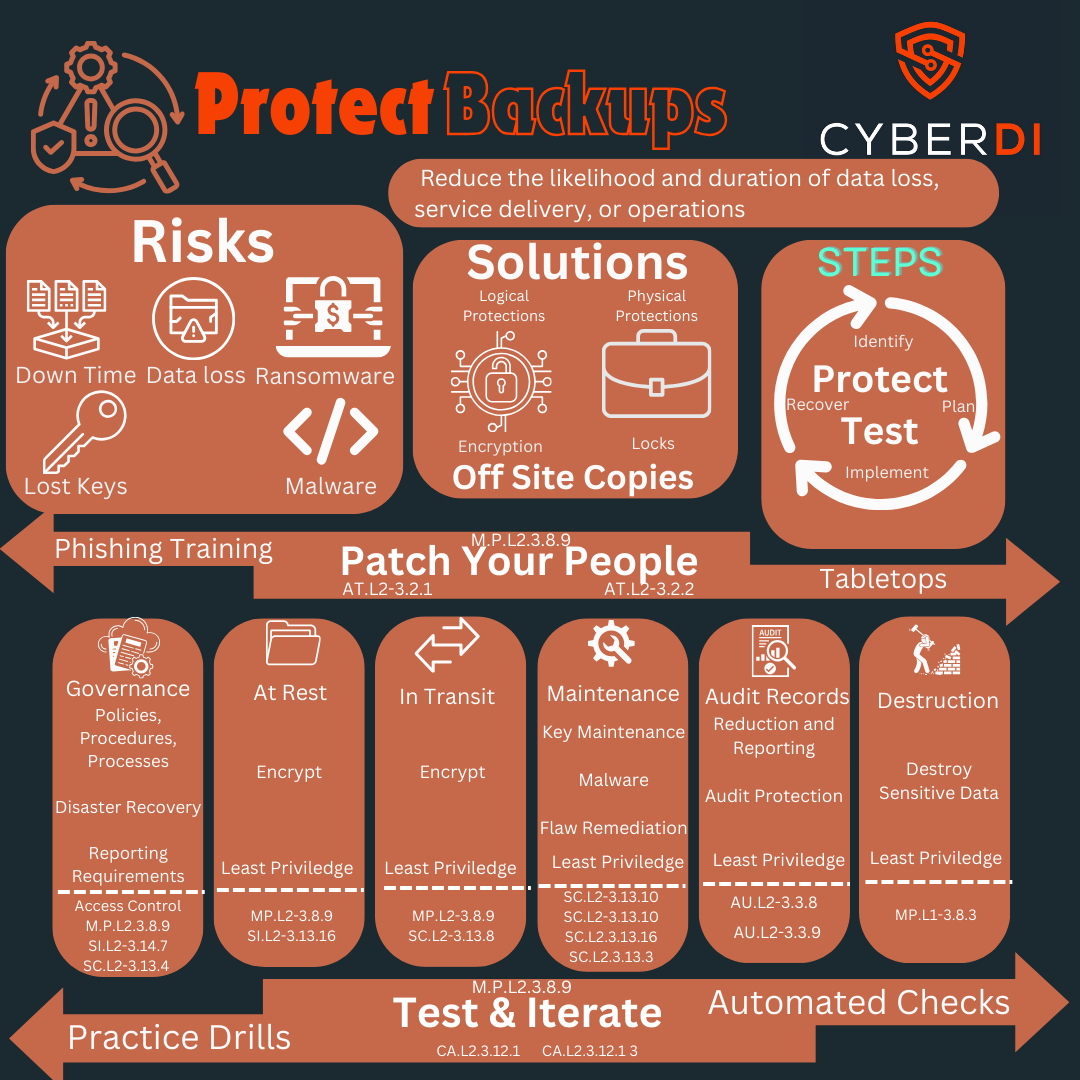
-
For almost every small business you will land on a cloud backup solution.
These do not come without risk. You need to document in your system security plan how you mitigate these risks
Encryption, MFA, and Least Privileged
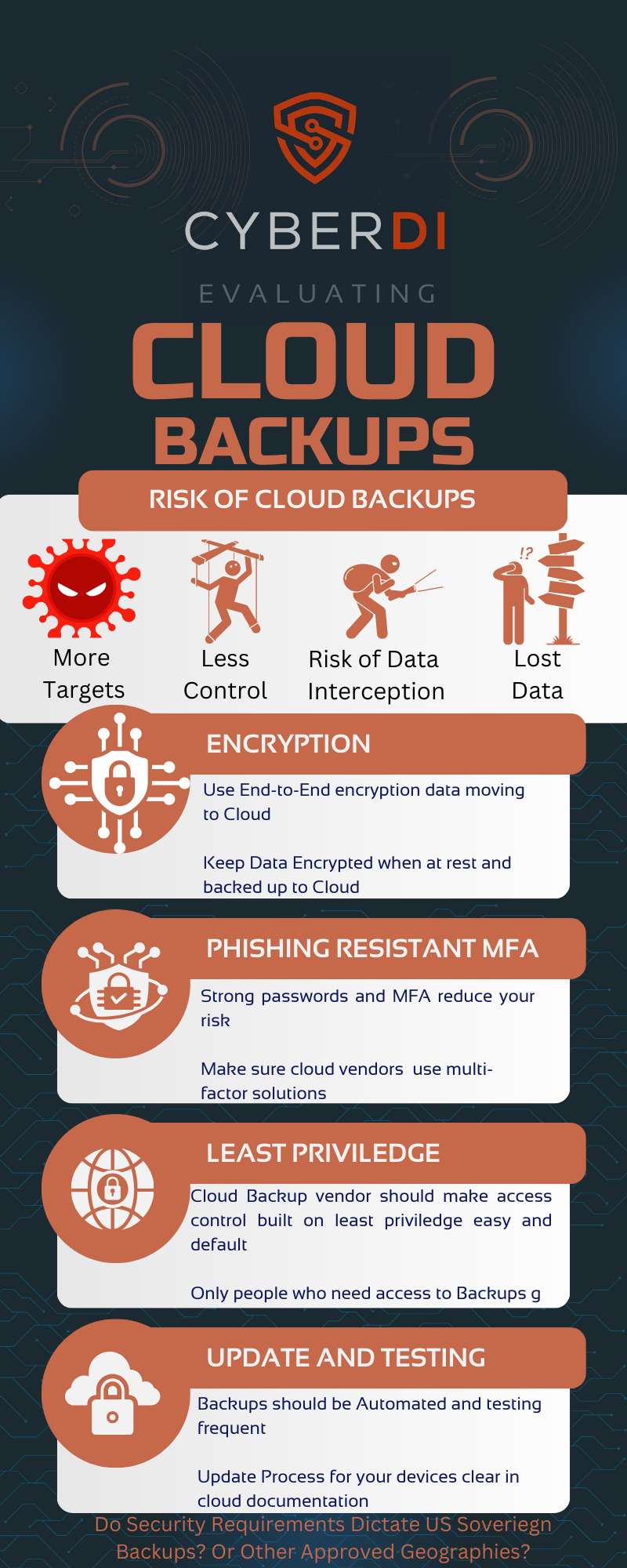
-
Chances are your Managed Service Provide or IT shop handles much of your backup, but you are responsible for the risk
Decisions belong to you. As you decide on the media types you need to understand the risk associated with the storage solution and shared responsibilities.
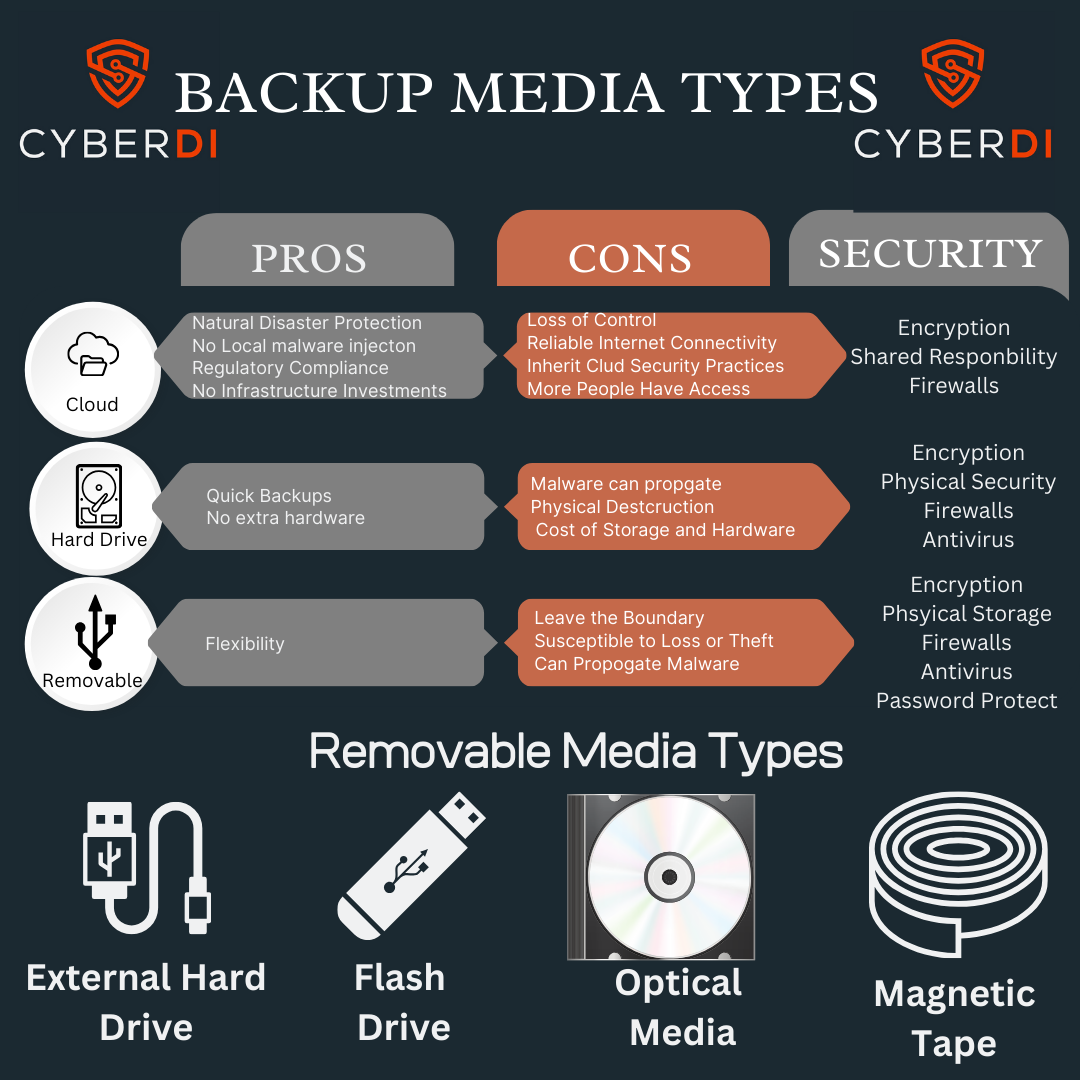
-
As you craft policies and procedures think about a 3-2-1 Backup strategy for your sensitive files
You want three copies
You want two different media types
You want one off-site copy of anything needed for emergency restoration

-
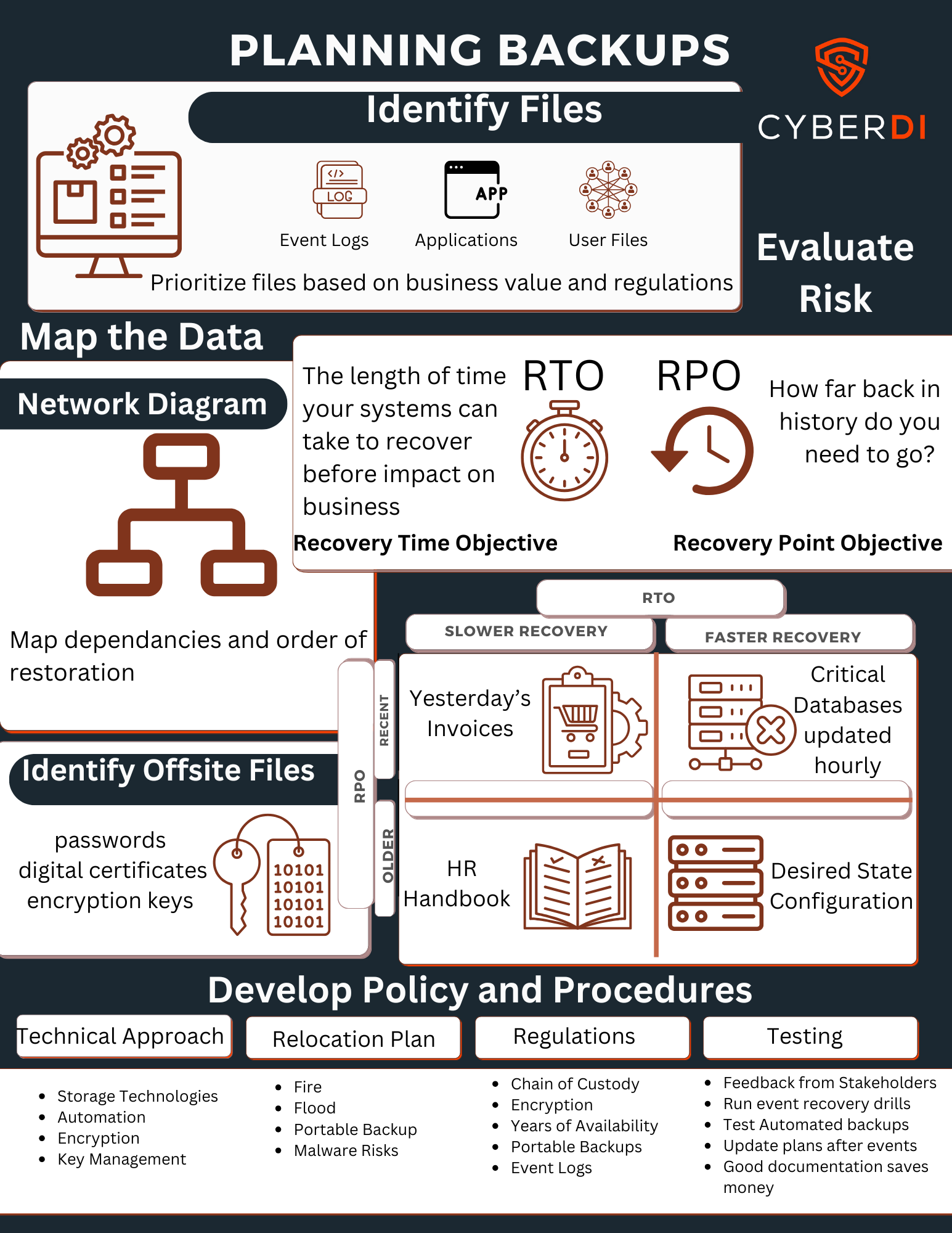
Start now
You need to identify the important files you handle and evaluate the common risks to those assets
Know how the data moves, and decide how long you can be down, and how far backups need to go.
Then develop procedures to make sure the plan is done and tested
-
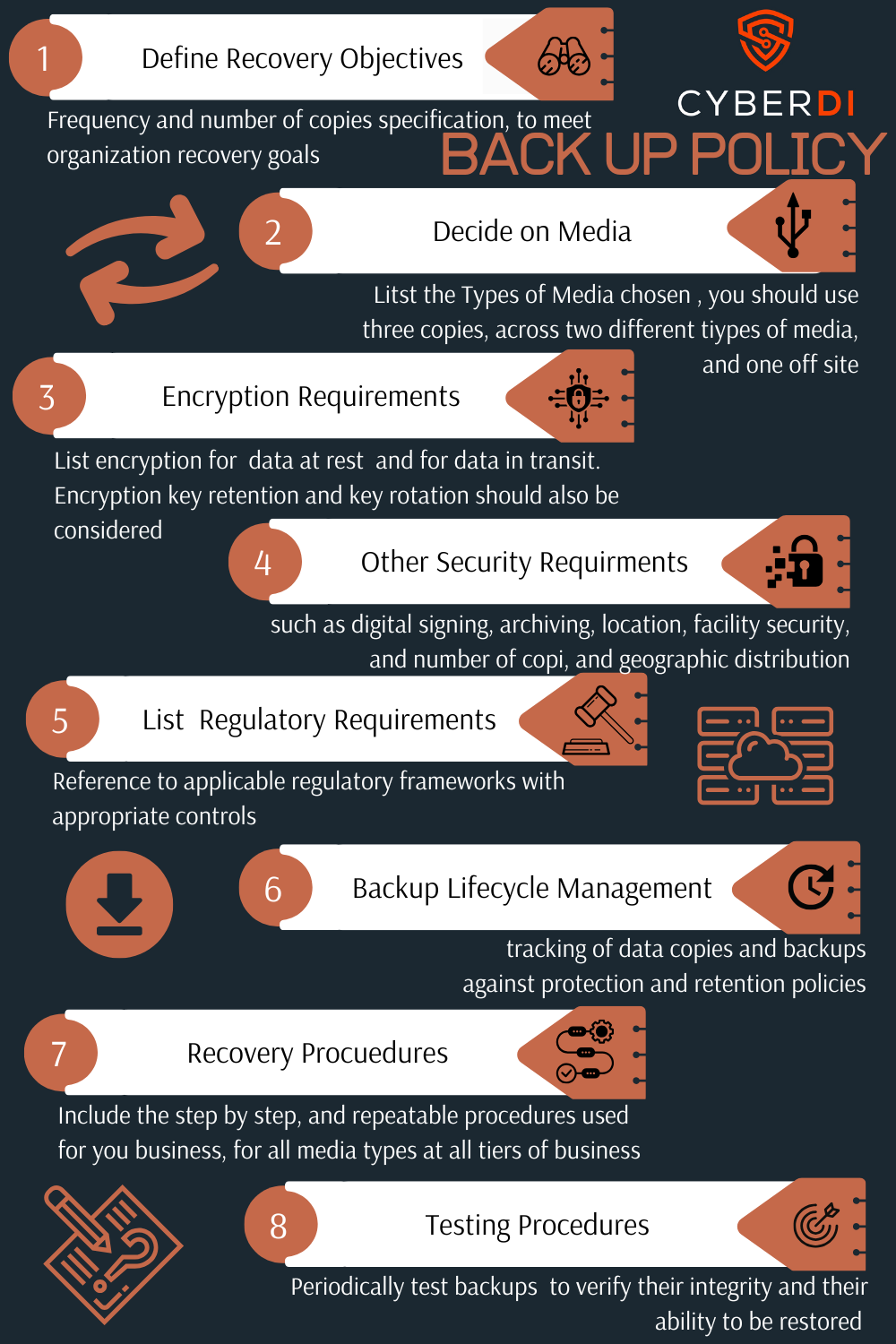
All of this should be documented in your backup recovery plan.
Just choosing a vendor is not enough. Your back up and recovery plan should cover these eight elements
-
And if your business is considered critical infrastructure
or if you want your insurance to be worth the money you pay.
You need good backups, by demand of law and lawyers
And it means more than just hiring a Cloud Company.
You need to plan

-
Under the new ZTA guidelines established by OMB M-22-09: Agencies must use strong MFA throughout their enterprise. This means all agency staff, contractors, and partners use phishing-resistant MFA for privileged access and soon, all access.
For public users, phishing-resistant MFA must be an option. Meaning signing into a government website to do your taxes
For most of your basic insurance needs, not including your sensitive data, any MFA will probably suffice

-
The US Government has required MFA for decades
Executive Order 13681 back in 2014 "Improving the Security of Consumer Financial Transactions" made MFA required for access to digital applications containing personal information.
NIST published SP 800-63-3 in 2017 and MFA was required to access to any personal information. They recommend phishing resistant MFA and require it for the most sensitive data.
In 2021 EO 14028 "Improving the Nation’s Cybersecurity" required All US government agencies required to implement MFA.
Then in 2022 we moved to a ZTA philosophy OMB M-22-09 and MFA now required throughout the federal enterprise.
But now insurance demands it, so you need it too.
-
Stronger MFA relies on asymmetric key cryptography. This protects from phishing attacks.
In fact in NIST- SP-800-63-3 NIST sets requirements to cryptographic authenticators such as PIV/CAC, FIDO U2F authenticators, or FIDO2/WebAuthN.
Those are fancy two dollar words to mean a different channel for your authentication mechanism that is always encrypted.
People can't social engineer the encrypted token because the user don't know it

-
Not all MFA is Equal
Yes Multifactor Authentication always provides greater protection than simple a username and a password but the mechanisms exist on a scale.
For most small businesses enabling MFA will be enough. Others who handle sensitive data maybe required to use more stringent MFA that is resistant to Phishing attacks
Take phone calls are SMS messages. These are vulnerable to hacking and aren't allowed on Federal systems. My university, on less secure data, allows SMS authentication
These are called shared secrets, like one time passwords, and they are vulnerable to phishing
-
In order for you to meet the MFA requirements of your Insurance Company you can't just enable MFA in Microsoft or Google.
You need to identify system users, you need to what processes access your system, and what devices connect to your system.
Like all things cyber this begins with Good Governance.
You should have an identification and authentication policy. You should have an HR guide that lists the procedures used to add or remove users from your company. Your employee handbook should cover the password policy, and your training needs to cover MFA.

-
No single factor is ideal for authentication. Multifactor authentication to a system uses two or more of the mechanisms.
Ideally you want them in different channels. For example you enter a username and password in one channel, but then a token is created in your authentication app on your phone.

-
Most of us have gone our whole lives using passwords as authentication. but we have four mechanisms commonly used to prove a user's identity.
-Something you know like a password -Something you possess. Like your ATM or MAC (for my Philly friends) -Something you are. Like a finger print Something you do. Like a voice print when you say, " My Voice Is My Passport Verify Me"
Multi-factor just means more than one

-
MFA, or multi-factor authentication, gets used in the process of how you identify users, their authorization levels, and then authenticate the users identity.
Authentication means proving a user's identity.

subscribe via RSS