CMMC: Systems Security Engineering and the Cloud

In systems security engineering requirements and constraints drive the design choices we make. They will send signals in a CMMC assessment. The constraints and requirements of an environment determines the type of evidence an assessor needs to verify. Organizations Seeking Certification and Certified CMMC Assessors will more than likely have to deal with many environments that utilize cloud deployments.
What is the Cloud?
According to NIST cloud computing enables, “ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) ,“ and that these resources take minimal configuration by the users.
The Federal Government, using this definition for their cloud migration efforts defined five key characteristics of cloud environments.
- on-demand service-Employees can access from any device
- broad network access-Employees can access anytime or anywhere
- resource pooling,-Employers share servers and infrastructure
- rapid elasticity-Can scale to almost unlimited users
- measured service-A third party maintains the system
Cloud computing provides a developer agnostic pathway to building controlled environments, meaning there are multiple solutions in a variety of forms of deployment. According to according to NIST this includes:
- Private Cloud- Provisioned for a single organization.
- Community Cloud-A cloud provisioned for specific groups of users withn a company
- Public cloud-provisioned for general community use and not used in business setting often
- Hybrid Cloud-A combination of any two above
Cloud Security Requirements
The shared services layer introduced into the system will impact the security engineered into the system and the assessment procedures used by a Certified CMMC Assessor. This service layer depends on the cloud service model used by the organization.
According to CISA’s Cloud Security Technical Reference Architecture the service model will determine security requirements.
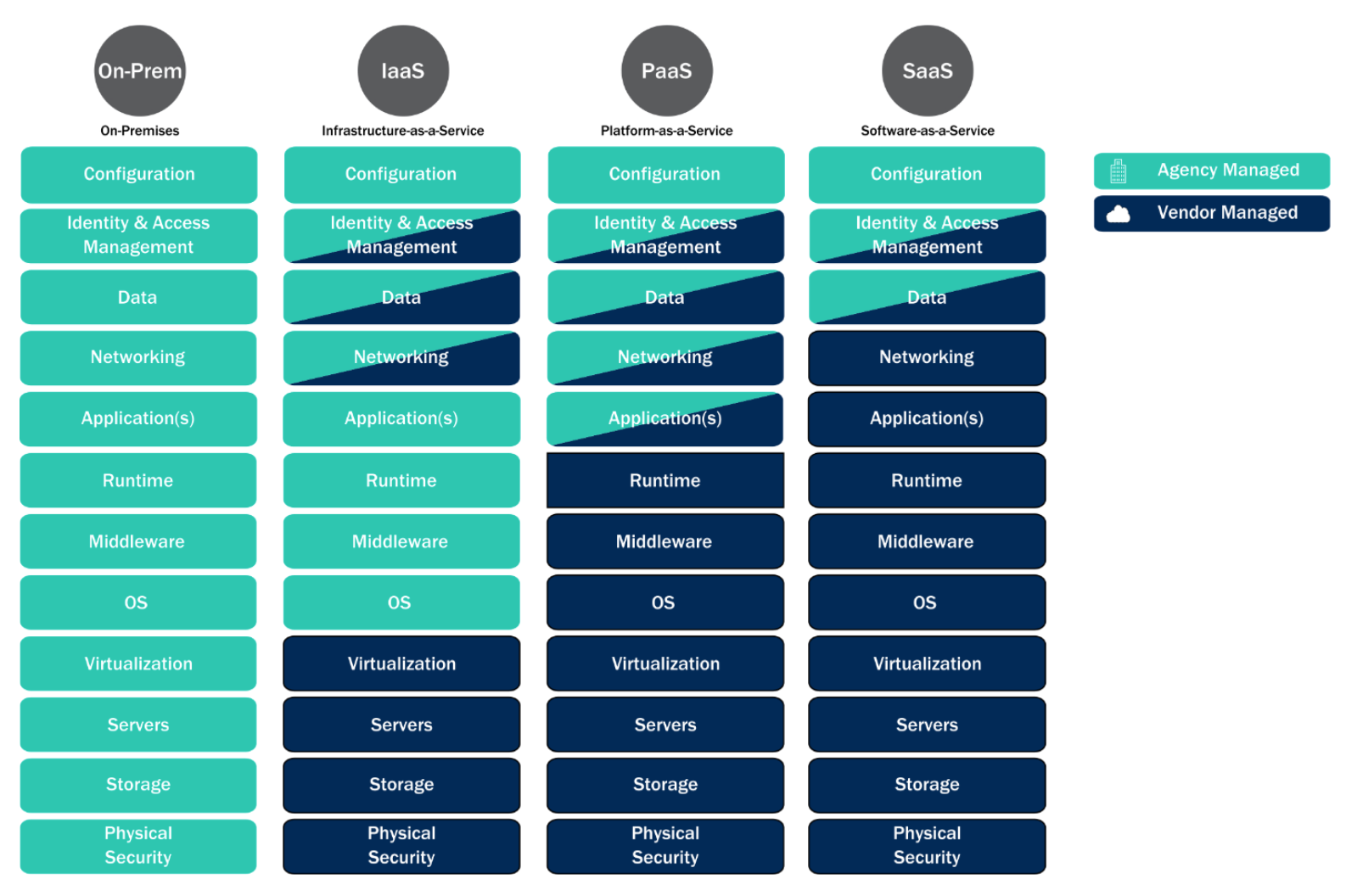
NIST defines four services models as illustrated in the figure from CISA’s Cloud Security Technical Reference Architecture:
- On-Premsises
- Infrastructure-as-a-Service
- Platform-as-a-Service
- Software-as-a-Service
Regardless of the service model all cloud environments must get engineered to meet the same basic security requirements as spelled out in Federal law and regulation.
Shared Responsibility Matrix
An assessor, in conversation with the OSC, must determine what and who is in scope. The majority of security requirements these assets introduce will all get documented in a shared responsibility matrix. An assessor will want to verify the FedRAMP equivalency seeing a document that outline who manages what security requirement if the cloud assets store, transmit or process unencrypted CUI. All cloud deployments, regardless of the service model, require a shared responsibility matrix for a CMMC assessment. Any FedRAMP authorized CSP must submit a responsibility matrix as part of their authorization package. Many organizations use that document to build their CMMC 171 SRM.
NIST-SP-800-171
These service models influence the security requirements engineered into a system and move the shared responsibility of meeting the requirements from the Organization managing them to the vendor managing the requirements. Regardless of the shared service layer engineered into the system the Organization Seeking Certification is always responsible for documenting and meeting the requirements.
Export Control
If an organization holds export-controlled data under ITAR or EAR new security requirements get introduced. This data requires data sovereignty for the cloud or must meet encryption requirements inside of a controlled environment and then remain encrypted the entire time in the cloud. Meaning never available in a readable format to anyone until downloaded and unencrypted back in the controlled environment. Only the organization and not the vendor should hold the keys to the data. Any vendor support must get restricted to US persons.
FedRAMP-Moderate
Cloud services, based on DFARS 252.204-7012(b)(2)(ii)(D), that store, process, or transmit Controlled Unclassified Information must meet the FedRAMP Moderate baseline or its equivalent. Thus if an organization uses a cloud service to support security such a s a SIEM, that tool does not need FedRAMP Moderate equivalency because it does not store, process, or transmit CUI.
Incident Reporting
In scope cloud service providers that store, process, or transmit CUI must also meet the incident reporting requirements of DFARS 252.204-7012(c-g). Any incident must get reported to the Department of Defense within 72 hours and images of the system must get preserved for 90 days. The DoD may want access to the equipment. This means a Cloud vendor must accept the contractual flow down of DFARS 252.204-7012
A CMMC assessment only verifies the trustworthiness of 171 security requirements. It is not a DFARS or EAR compliant assessment. That being said an assessor may verify if your Incident Response Plan meets DFARS requirements. If your policy and plans state you are in compliance with other security requirements the assessor will verify the procedures and evidence to ensure “you say what you do and do what you say.”
Cloud Environmental Constraints
Migrations take time if an organization thinks they may hold CUI in the future. A Prime contractor may demands compliant environment regardless if they flow CUI down to an organization in a contract. In these situations an OSC should consider a compliant cloud environment given the time migration takes. Time is often the toughest constraint in systems security engineering.
Regardless of deployment, cloud often refers to connecting to servers maintained by other organizations. How an organization utilizes the cloud depends on stakeholder needs and system constraints. A company inherits, or shares much of the security responsibility with a cloud vendor. This often gets represented in a shared responsibility matrix.
Thus an Organization Seeking Certification and a Certified CMMC Assessor will need to understand how employees connect to the cloud based infrastructure. Security requirements around encryption are very specific in CMMC. The baseline policies must apply constraints on users in how they access the cloud. You must also determine if a managed service provider is in scope and if they have access to the CUI stored in the CSP.
The world of IT, or Information Technology, has faced monumental shifts in the last three decades. We have moved from fixing a spool on a dot matrix printer to proving audit logs on endpoint detection.
From a Systems Security Engineering perspective, this changing relationship between IT companies and members of the Defense Industrial Base introduces to requirements and constraints on security of your business.
When creating a system for the way Controlled Unclassified Information flows through your networks an Organization Seeking Certification must understand the difference between key partners. Incorrect decisions could leave a third party and their systems in-scope of your assessment. This not only greatly increases costs but puts data at greater risk. The service models depend upon the people behind them.
CSP, MSP, MSSP What is the difference?
Utilizing NIST definition of cloud based computing we know that cloud solutions cut across five characteristics, three service models, and four deployments
| Characteristics |
Service Models |
Deployments |
|---|---|---|
| On-demand self-service Broad network access Resource Pooling Rapid Elasticty Measured Service |
Software as a Service Platform as a Service Infrastructure as a Service |
Private Cloud Community Cloud Public Cloud Hybrid Cloud |
This defines the software, but what about the people? CMMC-AB and NIST go out of their way not to define the difference between Cloud Service Provider, Managed Service Provider, and a Managed Security Service Provider. The scoping guidance refers to all external service provider the same and the NIST page lists the definition of Clous Service Provider as none.
NIST-SP-171-800 and CMMC scoping rely on a data centric model and the vendor delivering services does not change the security requirements. The people you choose to work with do change the evidence collection needs to meet the requirements and do introduce new constraints.
As an Organization Seeking Certification you need to consider these requirements and constraints as you evaluate partners. An Assessor will need to evaluate the requirements and contraints of an environment when developing assessment procedures.
What is a Cloud Service Provider?
A cloud service provider gives you access to computing networks and servers that they own and maintain. Google Docs SaaS that Google provides as a cloud service provider. Microsoft is a cloud service provider with different levels of security.
CSPS have their own requirements when it comes to establishing the trustworthiness in the system an Organization Seeking Certification throws. The evidence you must collect will change. Afterall Cloud Services Providers manage SaaS (Software as a Service), PaaS (platform as a service) or IaaS (infrastructure as a service) for users. This introduces new requirements and constraints to your system security engineering.
A cloud service provider hosts all of your data and thefore must meet the requirement of protecting CUI while in transit and at rest. Some types of CUI must require the data get stored in the United States. There are even requirements for cloud computing spelled out in Defense Federal Acquisition Regulation Supplemental.
What is a Managed Service Provider?
The contrast between MSPs and cloud services providers revolves around access control. MSPs manage and maintain technology that you own or license, whereas CSPs offer access to technology that they own. MSPs may manage both on-premises and cloud-based infrastructure for their customers. The MSP, however, does not own or control the underlying cloud infrastructure that stores your data or Controlled Unclassified Information.
MSPs also have their own requirements when it comes to developing evidence for compliance with CMMC Practices. They often act as IT Departments for companies that do not have them. An MSP acts as a partner and they may handle important tools such as Active Directory, data backup, anti-virus, and other IT functions. All of these fall in scope in a CMMC assessment.
Whether an MSP falls in scope of your assessments will depend on the services they provide. Some my partition systems but through asymmetric key encryption never have access to any credentials or assets. Other MSPs may have physical access to networks and a company may treat these technicians as in scope employees. The service level agreements and shared responsibility matrices will drive your security requirements.
What is a Managed Security Service Provider?
A managed security services provider (MSSP) provides oversight of specific security tools. These tools may not store or access CUI but they protect assets that do fall in scope. An MSSP focuses security services, such as firewalls, virus protection, and intrusion detection, They may provide a SIEM, or Security information and event management. MSSPs often specialize in a particular area, such as managed firewall service providers.
According to the CMMC Level Scoping Guide “Security Protection Assets are part of the assessment scope and are required to conform to applicable CMMC practices, regardless of their physical or logical placement.”
The scoping guidance spells out that an MSSP falls in scope for all-applicable CMMC practices. Yet the same can be true of a CSP or MSP as well.
As you apply systems security engineering to meet the requirements of a CMMC assessment you must evaluate your partners. Examine the service level agreements you have, consider the time of deployment and migrating between a cloud or service provider. You need to choose compliance partners when evaluating vendors.
What is Hybrid?
A hybrid deployment combines onprem servers with cloud-based servers. Some organization may want to keep control of servers that store credentials for cloud computing. Others may have out of scope on prem servers they maintain but provision a private cloud for employees authorized to handle Controlled Unclassified Information.
A hybrid cloud infrastructure may connect to a public cloud platform from a trusted third-party provider. Hybrid deployments may also utilize a private cloud partitioned on premises. A company may utilize hosted private cloud provider and allow employees to connect to the servers. A CMMC Assessor will often find an in-scope managed service provider may maintain the hybrid environment.
Hybrid Environmental Requirements
Like all environments the hybrid cloud must meet the same security requirements. The use of the hybrid environment just changes the metrics and evidence used to ensure the security requirements of NIST-SP-800-171.
The people who maintain the environment introduce evidentiary requirements. Any on-prem deployment of tools will need a focus on the privileged users who can access those tools. Hybrid deployments can either introduce the most complicated requirements to document or help an organization shrink their scope by utilizing a cloud-based service. They are difficult to maintain but can provide benefits to those who take advantage of increased on-prem solutions with the scalability of cloud services.
For example, you will need to think about the access to both the logical and physical barriers that store servers. A company will need to make sure their inventory disposal polices align with the requirements set out in the Media Protection domain. Many smaller companies may try to utilize a hybrid approach managed by an MSP. Some organizations keep their access control logs and Identify Managament systems onprem and data in the cloud. This will impact the evidence collected to demonstrate security requirements get met.
An MSP may or may not be in-scope or have access to your Controlled Unclassified Information in an unencrypted state. If they provide security to systems that protect CUI either on-prem or in the cloud you will need to show how the MSP handles the applicable security requirements they manage.
Hybrid Environmental Constraints
Hybrid environments can bring all the environmental constraints of on-prem or cloud deployments while leaving a managed service provider in scope. On the other end of the spectrum hybrid environments in a private cloud using asymmetric keys for authorization can shrink a company’s scope down to a few assets.
The difficulty in maintaining hybrid environments introduce many constraints. First you need to make the relationship and boundaries visible in all your data flow and network diagrams. Cost and time always act as constraints in systems security engineering. In hybrid solutions you may have to support two disparate solution who do not “talk computer together.” This introduces bespoke coding and architecture that presents a new threat vector. If these systems have data interoperability constraints even more challenges get introduced.
At the same time Hybrid solutions can often help small businesses who may have only limited exposure of CUI in their on-prem environment. So if a manufacturer only had two to three machines that process CUI they may utilize a hybrid environment to share controlled technical information with remote employees. The CUI gets encrypted before it goes to the remote employee. The remote employee only works on a local device not connected to their network. They rencrypt the file before sending back within the onprem physical boundary.
Hybrid environments managed by high quality MSPs can provide flexibility, reduced cost, and the ability to scale.
What is On-Prem?
An on-premises environment, often on-prem for short, means all in scope software and systems exist withing the physical and logical boundaries of an organization. The organization seeking certification is responsible for managing, maintaining, and supporting all systems and the security of the assets who access those systems to process, store, or transmit Controlled Unclassified Information.
On-Prem Environmental Requirements
On-Premises environments can bring the same regulatory and security requirements of Cloud and Hybrid deployments but the organization is responsible for managing all the security requirements of the software and hardware. The vendor has no responsibility.
The network diagrams and data flow diagrams will dictae what evidence a Certified CMMC Assessor must collect to assess on-prem environments. An IT department or External Service Provider must maintain layers security, encryption, and protection of key boundary points.
On-Prem, however, is not a unified deployment. Companies may have multi-site environments that connect to these systems. Overall on-site staff or contracts must maintain all software, hardware, access control, and physical security. This introduces specific evidence requirements for a CMMC assessment.
On-Prem Environmental Constraints
A company maintains all the servers, firewalls, and routers. The necessary resources create a sever constraint on maintenance. The cost of deprecating equipment may have advantages to cloud environments. The over reliance on Managed Service Providers that maintain IT systems may increase the scope of security requirements.
NIST-SP-800-171 approach to security relying on logical and physical boundaries meets the constraints of on-rem deployments for many companies. However recent security guidance and costs often drive businesses towards the cloud.
Considering the ease of compliance for on-prem deployments may influence the design decisions and organization seeking certification makes. Other companies may choose on-prem solutions out of sheer size of their organization. A Certified CMMC Assessor will need to pay attention to the privileged access users have to key boundaries that protect physical access to servers. Organization who utilize on-prem solutions, will also need to detail who maintains the security updates to any of these assets. Most importantly they will have a reference architecture that explains the separation techniques that protect CUI.
Right Fitting your Cloud Deployment
Almost all organizations will have some element of cloud in their systems. From a Systems Security Engineering persepective each service model impacts the requirements and constraints a company must consider in their risk based awareness plan and daily operations.
Systems Security Engineering broadcasts that an organization takes their security requirements serious regardless of the contrainsts they face.
This is the fifth post on using NIST-SP-800-160 Systems Security Engineering to meet the requirements of SC.L2-3.13.2 – SECURITY ENGINEERING
Employ architectural designs, software development techniques, and systems engineering principles that promote effective information security within organizational systems.
First post: Evaluating Organizations Seeking Certifcation: Document Based Requirements to Start a Conversation
Second Post: CMMC and Systems Security Engineering
Third Post: CMMC and Asset Inventory
Fourth Post: CMMC Assessment: In Systems Security Engineering the Environment Drives Evidence
Img Credit: lost in transmission flickr photo by savoryexposure shared under a Creative Commons (BY-SA) license