CMMC Infographics
A collection of Cybersecurity Maturity Model Certification Infographics you can utilize as quick reference or study guides. Some may even fit your awareness needs.
What is FIPS 140-2a
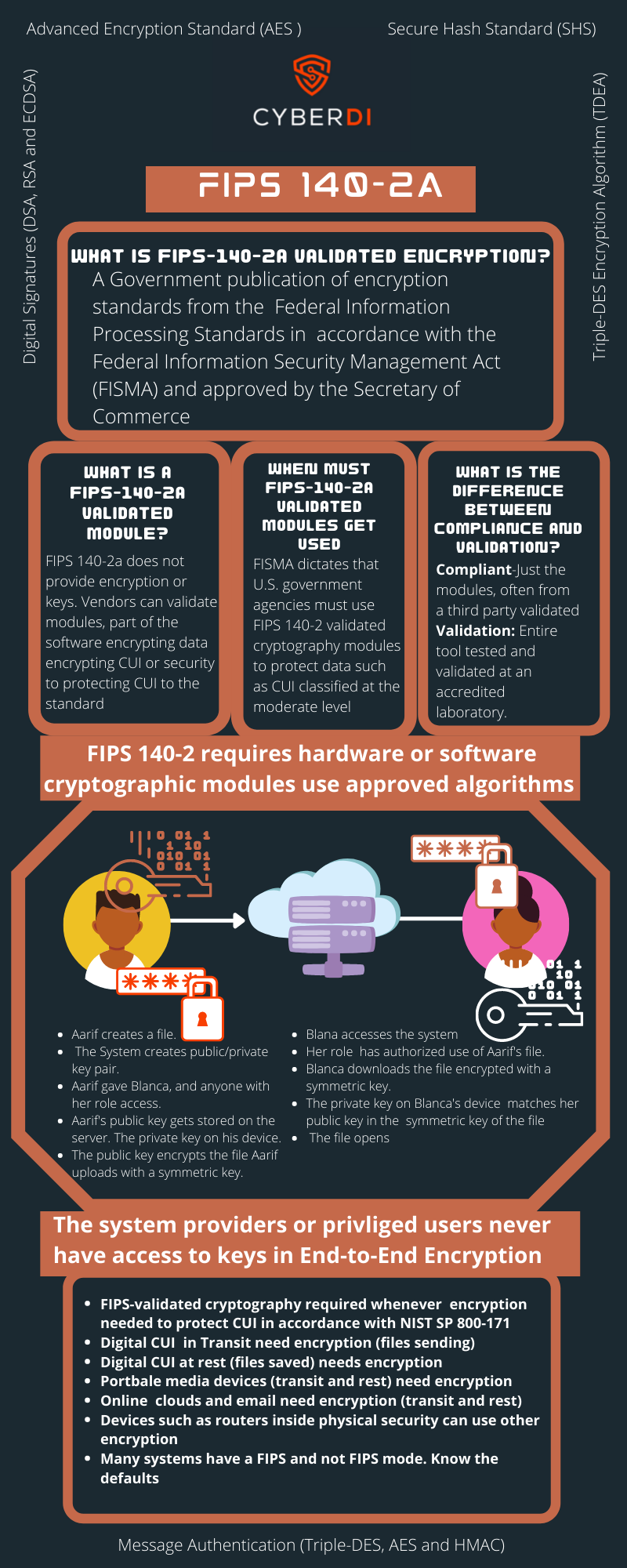
pdf version: https://jgregorymcverry.com/readings/FIPS1402a.pdf
Understanding the encryption requirements for NIST-SP800-171, and CMMC.
Work Stations and Controlled Environments
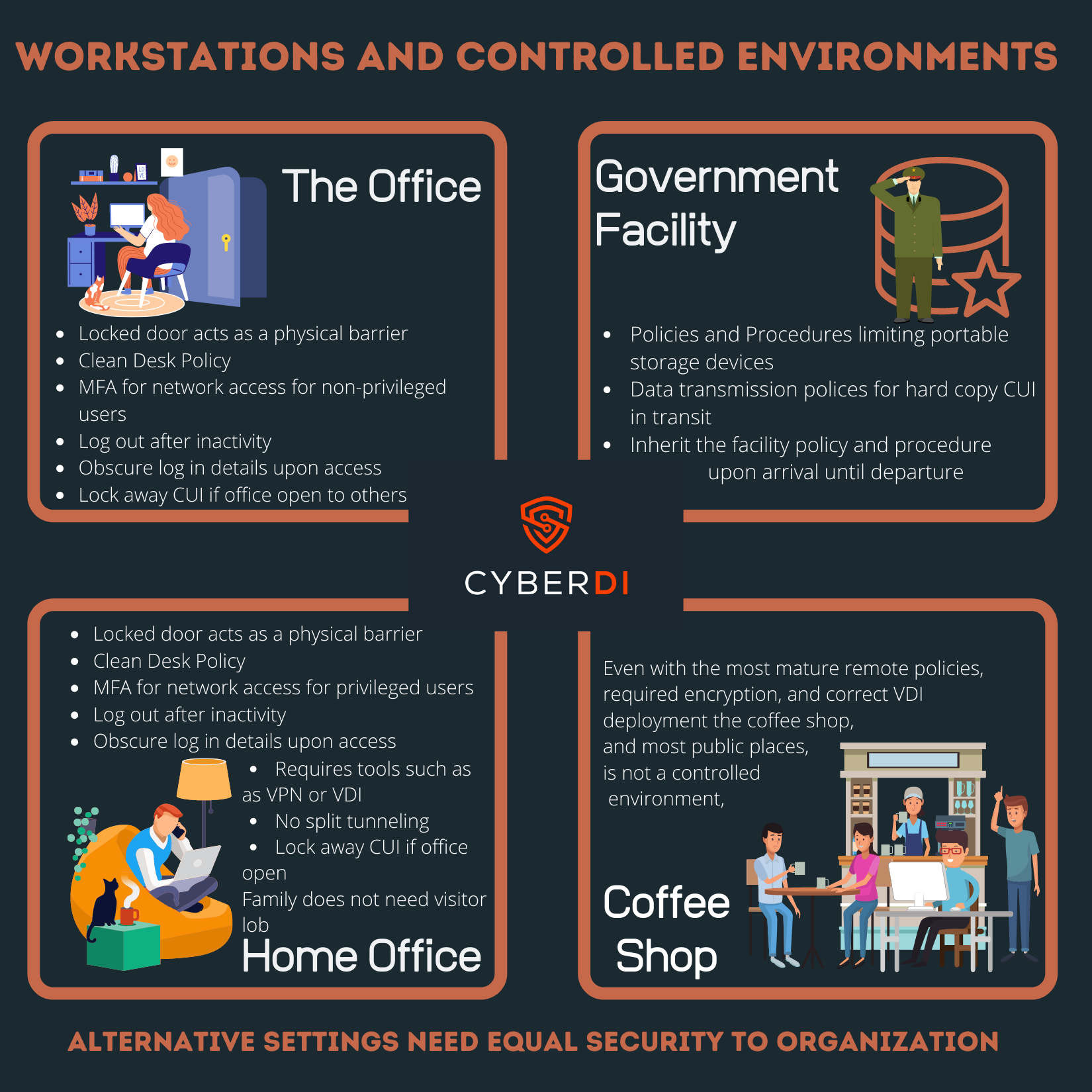
pdf version: https://jgregorymcverry.com/readings/WorkstationsAndControlledEnvironments.pdf
Protecting controlled unclassified environments requires an understanding of workstations. How do your employees create and enforce controlled environments so unatorized users can not oversee or over hear CUI?
DFARS Interim Rules and CMMC

pdf version: https://jgregorymcverry.com/readings/DFARSInterimRule.pdf
Understand how 7019 and 7020 impact your business during the CMMC 2.0 launch.
Destroying CUI
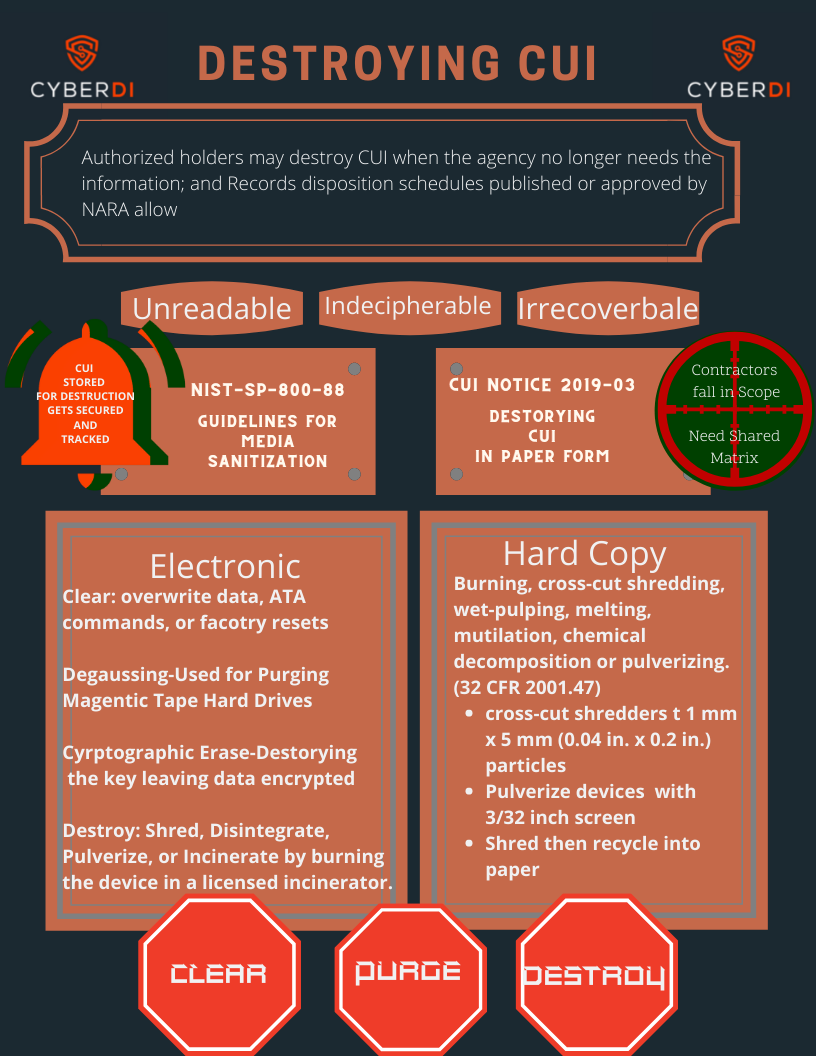
pdf version: https://jgregorymcverry.com/readings/DestroyingCUI.pdf
You must follow very specific policies from ISOO and NIST on the destruction of controlled unclassified information.
What is DFARS 252.204-7012?
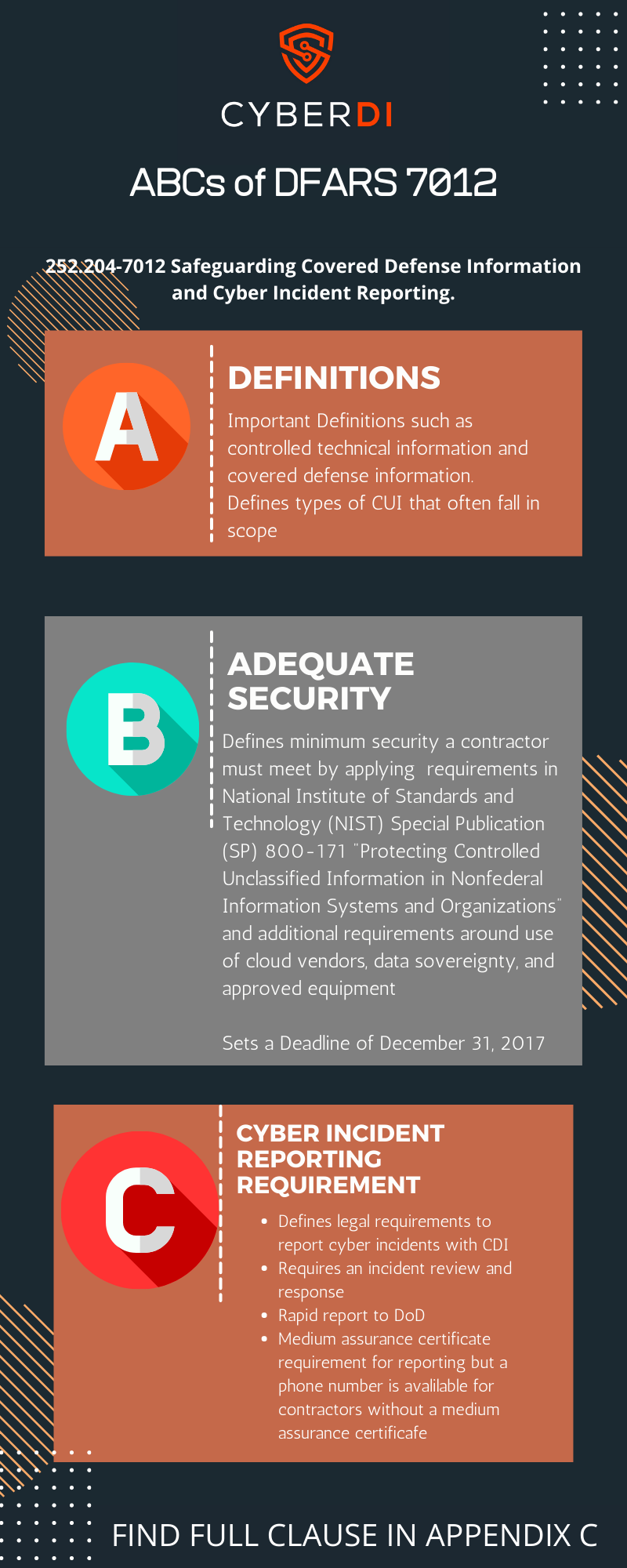
pdf version: https://jgregorymcverry.com/readings/DFARSABC.pdf
Learn the basics of the 7012 clause
Asset Categorization
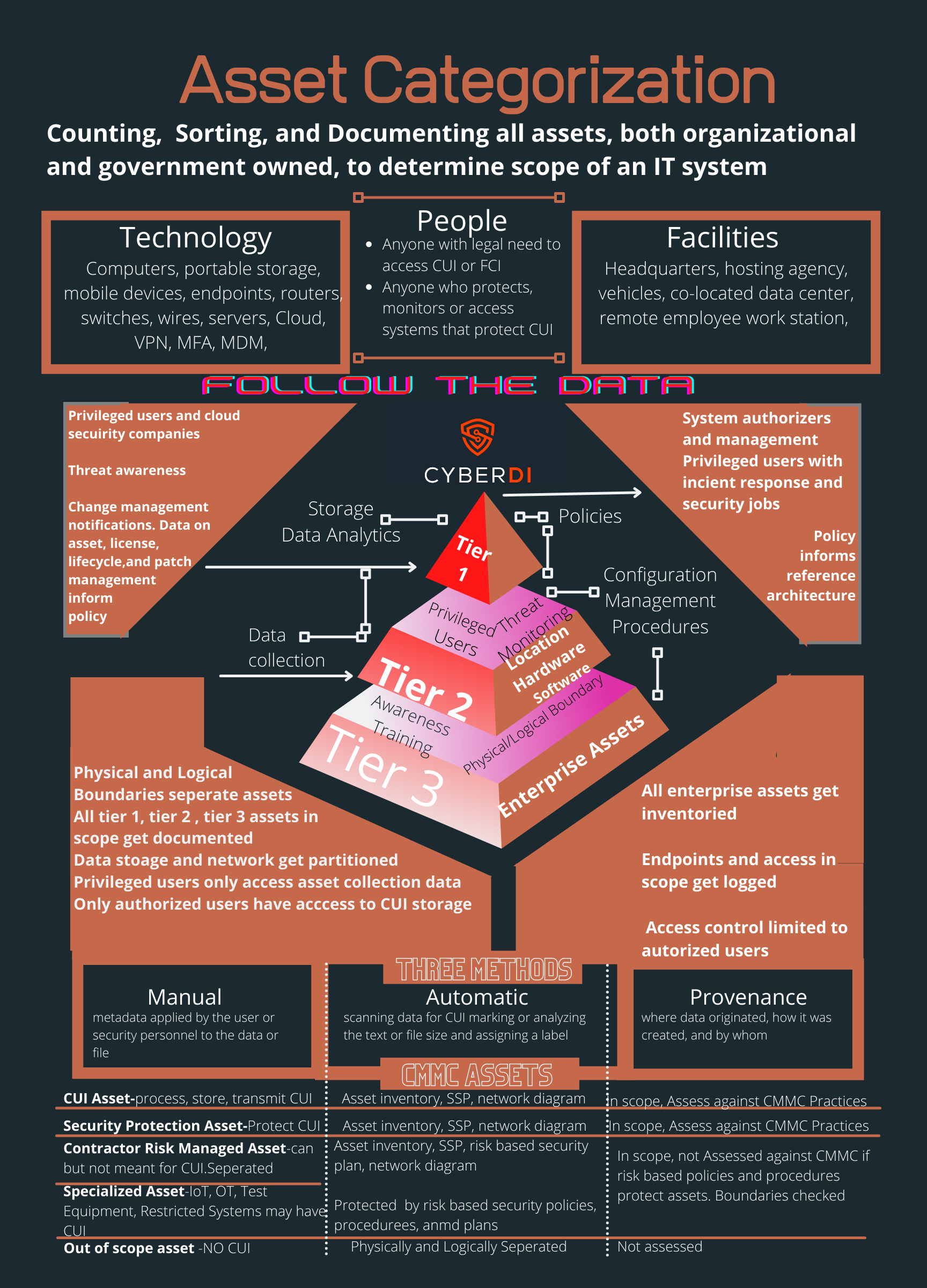
pdf version: https://jgregorymcverry.com/readings/CUIMarkingGuidance.pdf
The new CMMC scoping guidance makes asset categorization critial. Good Iventory and asset management and role based access make it happen.
Evaluating Internal Risks

pdf version: https://jgregorymcverry.com/readings/InternalRisk.pdf
84% of all breaches occur from internal threats. Often howver people doing bad think they are doing good. Creating a culture or growth, accountability, and respect can reduce the risk but you still should know the warning signs.
Introduction to FedRAMP
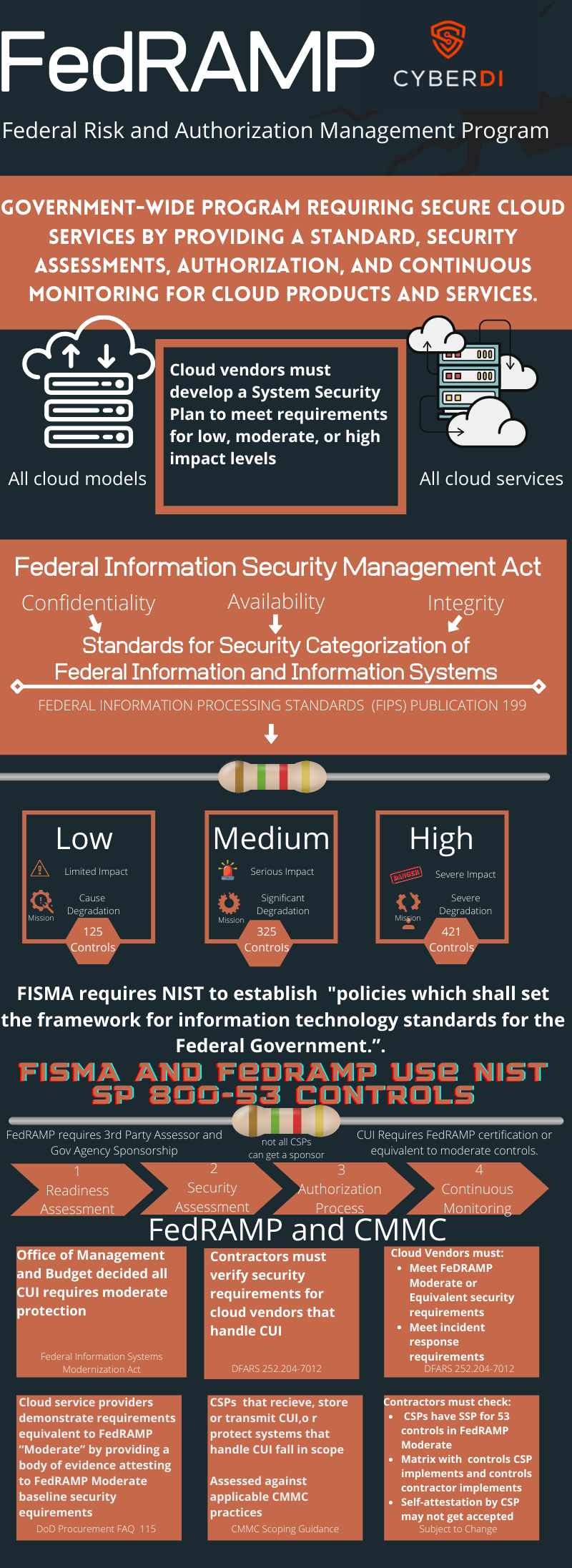
pdf version: https://jgregorymcverry.com/readings/FedRAMPIntro.pdf
An overview of the FedRAMP program. DFARS 7012 requires cloud vendors to reach FedRAMP Moderate or equivalent.
CMMC and Multifactor Authentication
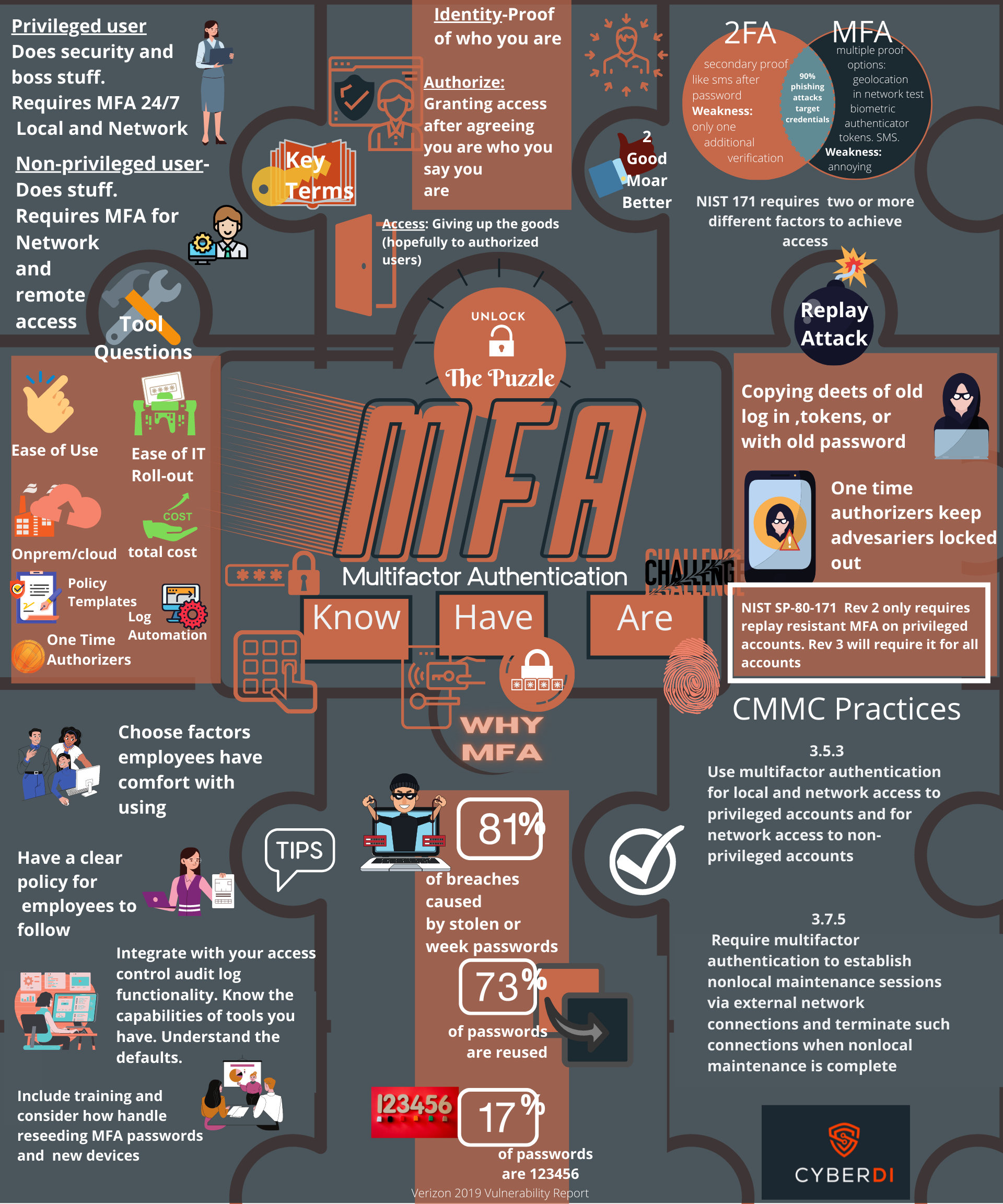
pdf version: https://jgregorymcverry.com/readings/MFA.pdf
Learn the basics of MFA and Cybersecurity Maturity Model Ceritification.
Alternative Markings and CMMC
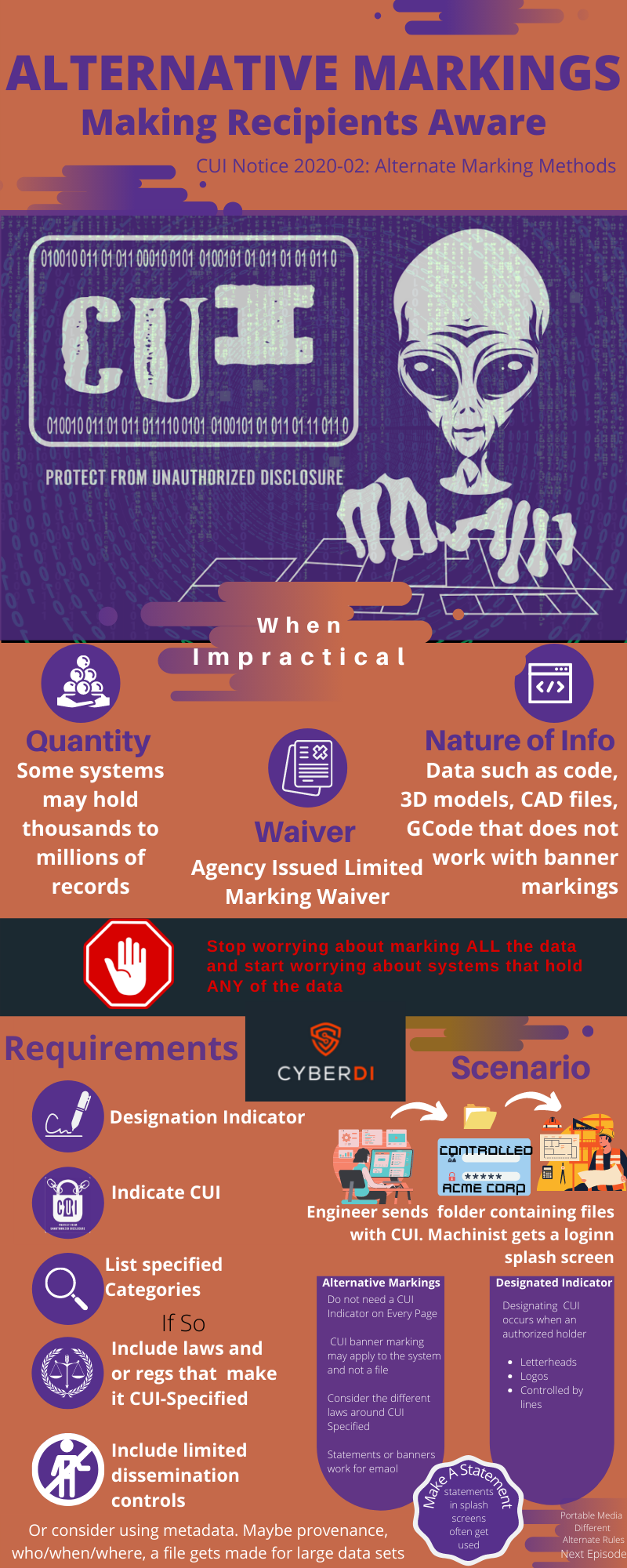
pdf version: https://jgregorymcverry.com/readings/AlternativeMarkings.pdf
We spend so much time worrying about the proper marking of each piece of CUI. Yet if a system holds one piece of CUI it falls in scope. Learn about CUI markings and modern data.
Controlled Unclassified Information Marking
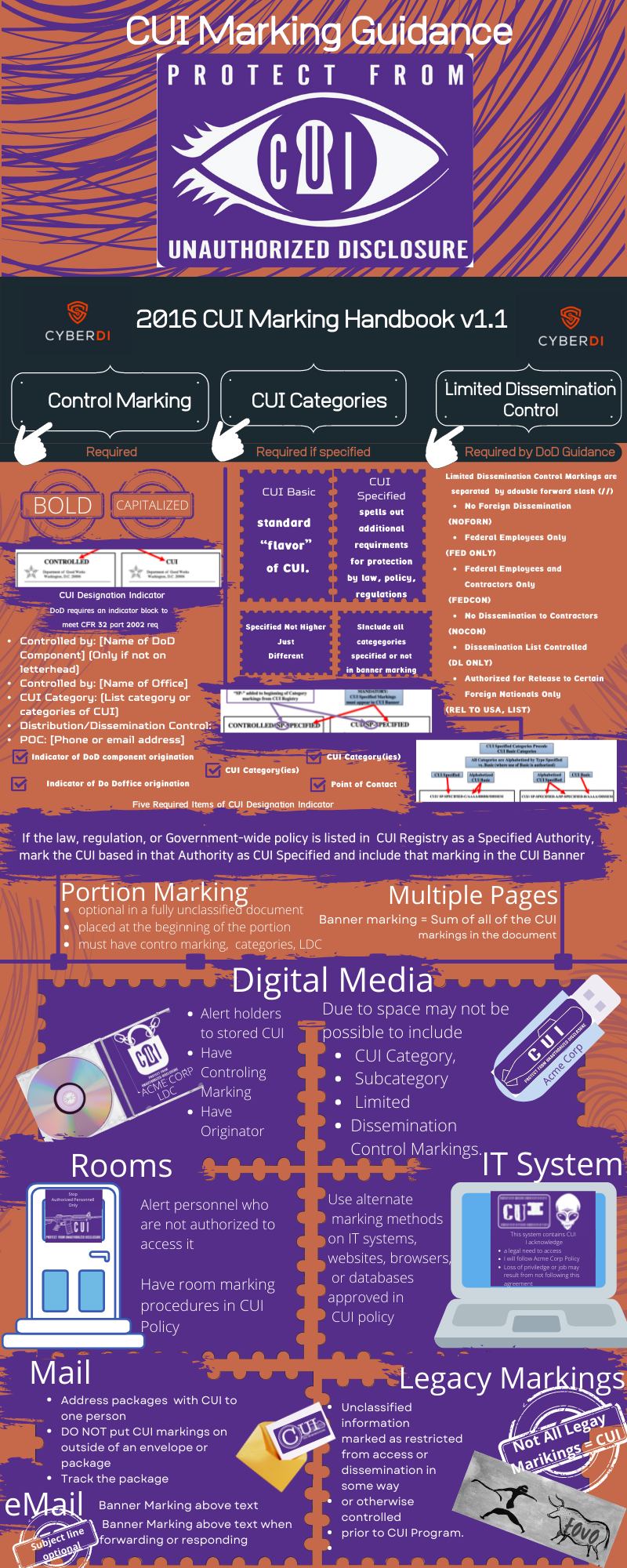
pdf version: https://jgregorymcverry.com/readings/CUIMarkingGuidance.pdf
Learn the basics of marking CUI per DODI 5200.48. and CFR 32 part 2002
Document Based Artifacts

The update to CMMC removed the process maturity objectives and policies and procedures returned to their lowly NFO status tucked away in Appendix E of NIST-SP-800-171.
Yes if you read the assessment objectives almost every CMMC practice requires specifications spelled out in document based artifacts.
pdf version: https://jgregorymcverry.com/readings/CMMCDocumentaton.pdf
CMMC Awareness and Training Videos
CMMC CUI Data Transmission Policy
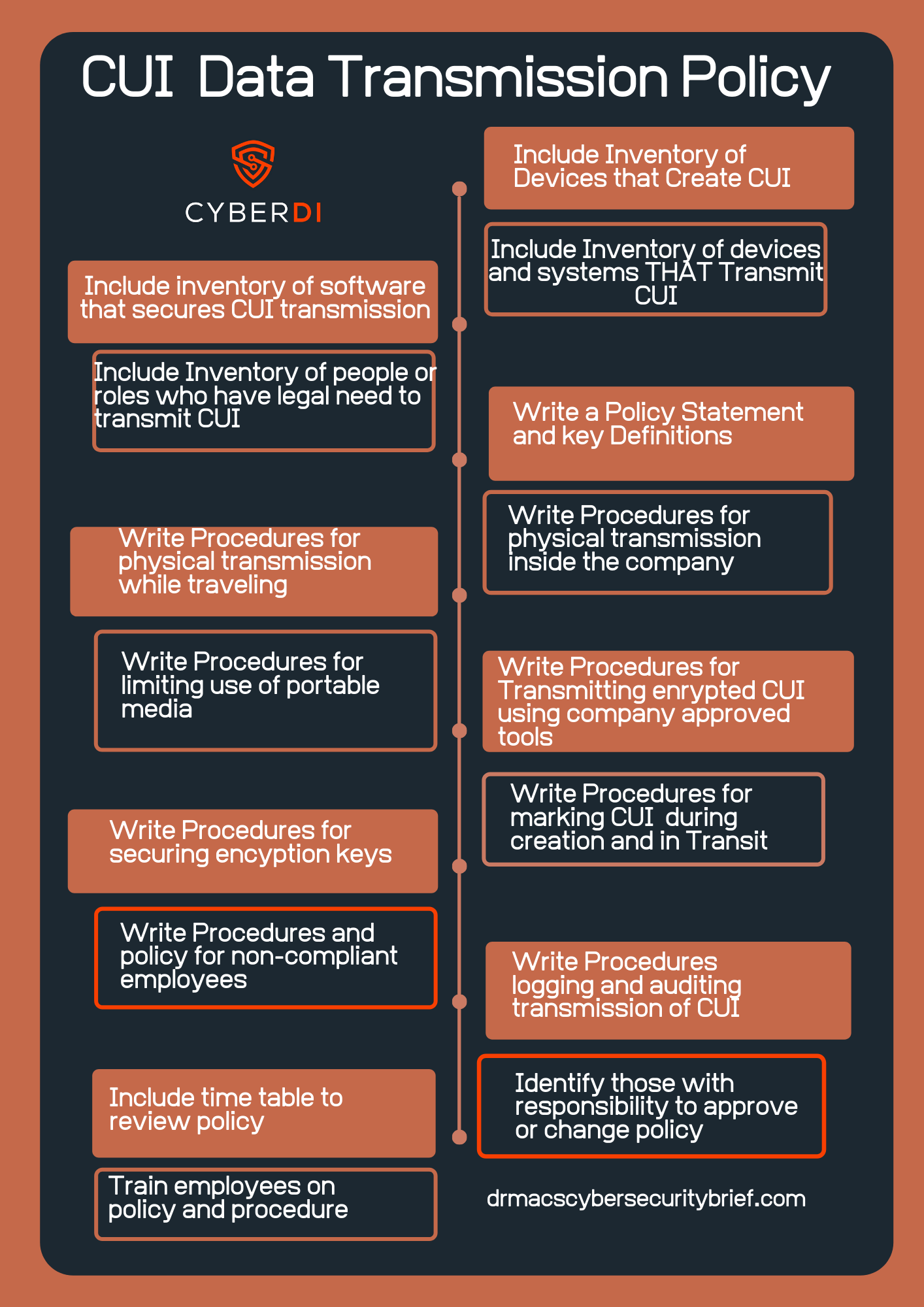
Having a clear understanding of how CUI moves through your system and then developing procedures for the transmission of CUI will help.
pdf version: https://jgregorymcverry/readings/CUIDateTransmissionPolicy.pdf
CMMC Scoping
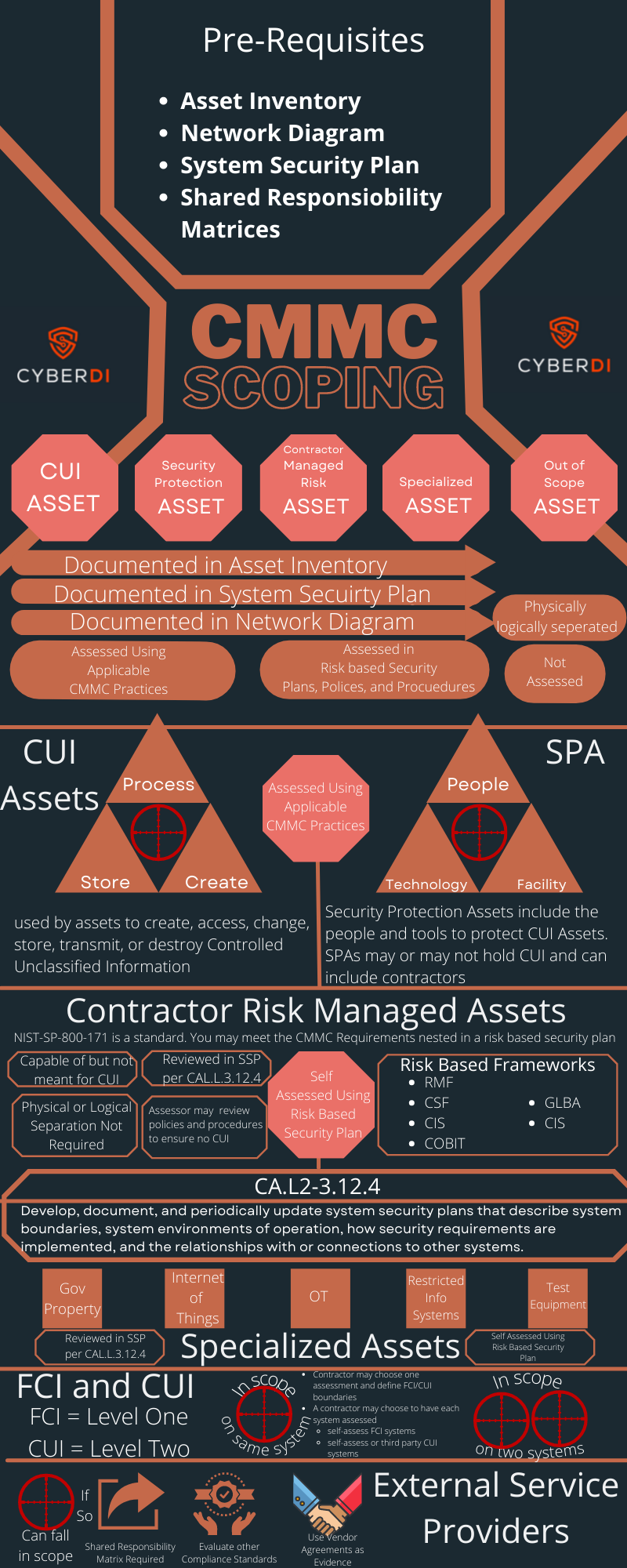
Understand the new CMMC scoping guidance. You can not get an assessment without an agreed upon scope. Many prequisites must get filled.
pdf version: https://jgregorymcverry/readings/cmmcscoping.pdf
CMMC Timeline
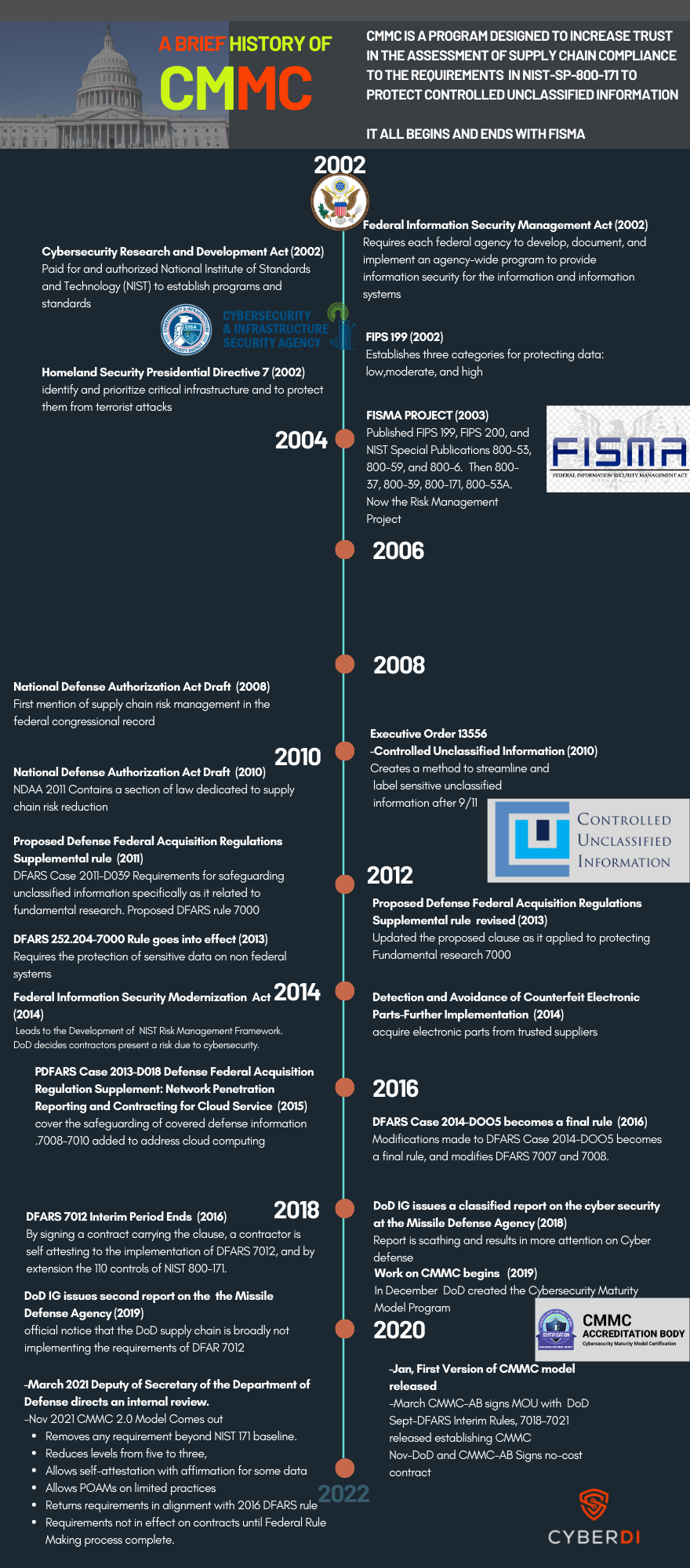
pdf version: https://jgregorymcverry.com/readings/CMMCTimeline.pdf